
Industry analysts and security practitioners unanimously concur that application security is a big deal. The application security market is predicted to exceed $7 billion USD by 2023 according to a recent research by Forrester. While Gartner says that banking sector leads in global cybersecurity spending.
This research guides you through application security, privacy and compliance of the world largest financial institutions from S&P Global list for 2019.
Key Findings
Compliance:
- 85 e-banking web applications failed GDPR compliance test
- 49 e-banking web applications failed PCI DSS compliance test
- 25 e-banking web applications are not protected by a Web Application Firewall
Security Vulnerabilities:
- 7 e-banking web applications contain known and exploitable vulnerabilities
- The oldest unpatched vulnerability is known and publicly disclosed since 2011
- 92% of mobile banking applications contain at least 1 medium-risk security vulnerability
- 100% of the banks have security vulnerabilities or issues related to forgotten subdomains
Table of Content
2. Website Security
3. SSL/TLS Encryption Security
4. PCI DSS and GDPR Website Compliance
5. Outdated and Vulnerable Web Software
6. Usage of Web Application Firewalls
7. Mobile Banking Applications
8. Phishing Campaigns
9. Trademark Infringement and Domain Squatting
10. Recommendations
Data Source and Methodology
We leveraged an enhanced methodology from our previous research that covered web and mobile application security of the world largest companies from the FT 500 list.
For the purpose of this research, we carefully studied external web applications, APIs and mobile apps of the S&P Global list that contains world largest financial organizations from 22 countries:
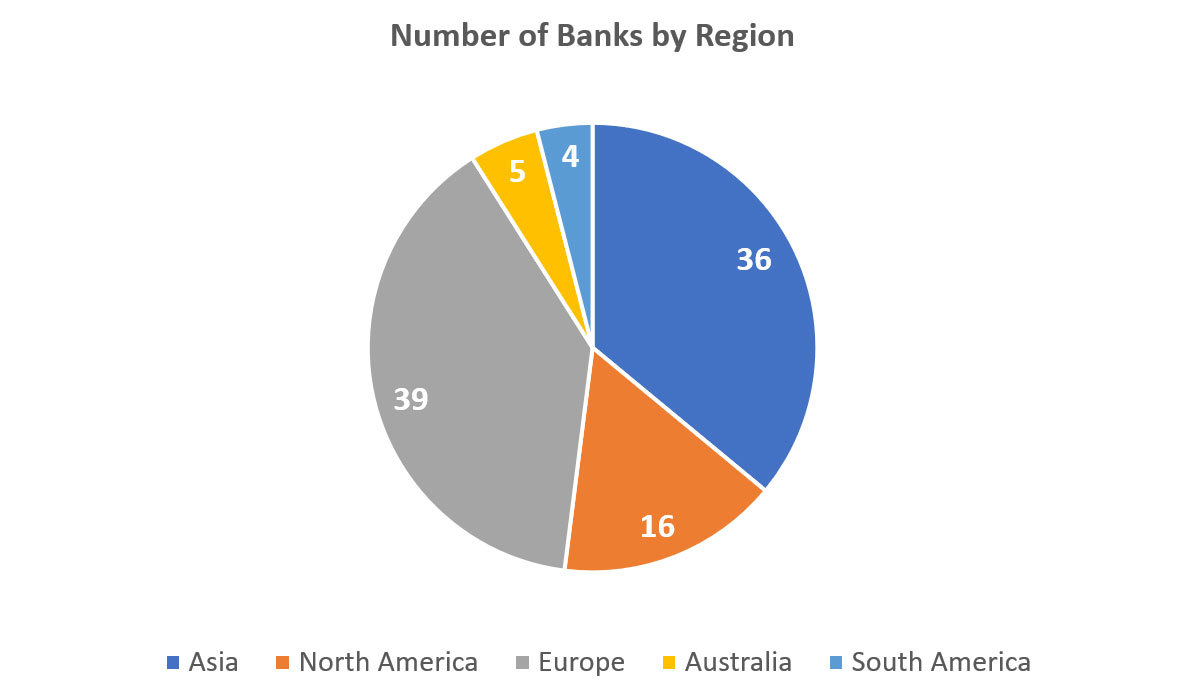
Diagram 1: Number of Banks by Region
The following external assets and applications were tested:
| Tested Assets | Quantity |
|---|---|
| Main websites (“www.”) | 100 |
| Subdomains | 2366 |
| E-banking web applications | 102 |
| Mobile banking applications | 55 |
| Backend APIs of the mobile banking applications | 298 |
We conducted various non-intrusive security, privacy and compliance tests provided by ImmuniWeb’s Community offering freely available online to the cybersecurity community:
- SSL Security Test [scoring methodology and list of checks]
- Website Security Test [scoring methodology and list of checks]
- Mobile App Security Test [list of checks]
- Phishing Test [list of checks]
PCI DSS compliance testing covered Requirements 2.3, 4.1, 6.2, 6.5 and 6.6 of the most recent version (v.3.2.1) of the standard.
GDPR compliance testing covered Article 5 Section 1, Article 5 Section 2, Article 6 Section 1, Article 6 Section 4(e), Article 7, Article 25 Section 1, Article 32 Section 1(a)(b)(d) and Article 35 Section 7(f) of the enacted regulation.
Non-intrusive Software Composition Analysis (SCA) of Open Source Software (OSS) verified fingerprinted software versions for publicly disclosed vulnerabilities from OWASP Top 10 list.
Website Security
Only 3 main websites out of 100 had the highest grades “A+” both for SSL encryption and website security:
- www.credit-suisse.com (Switzerland) A+
- www.danskebank.com (Denmark) A+
- www.handelsbanken.se (Sweden) A+
Below are website security grades for the main websites:
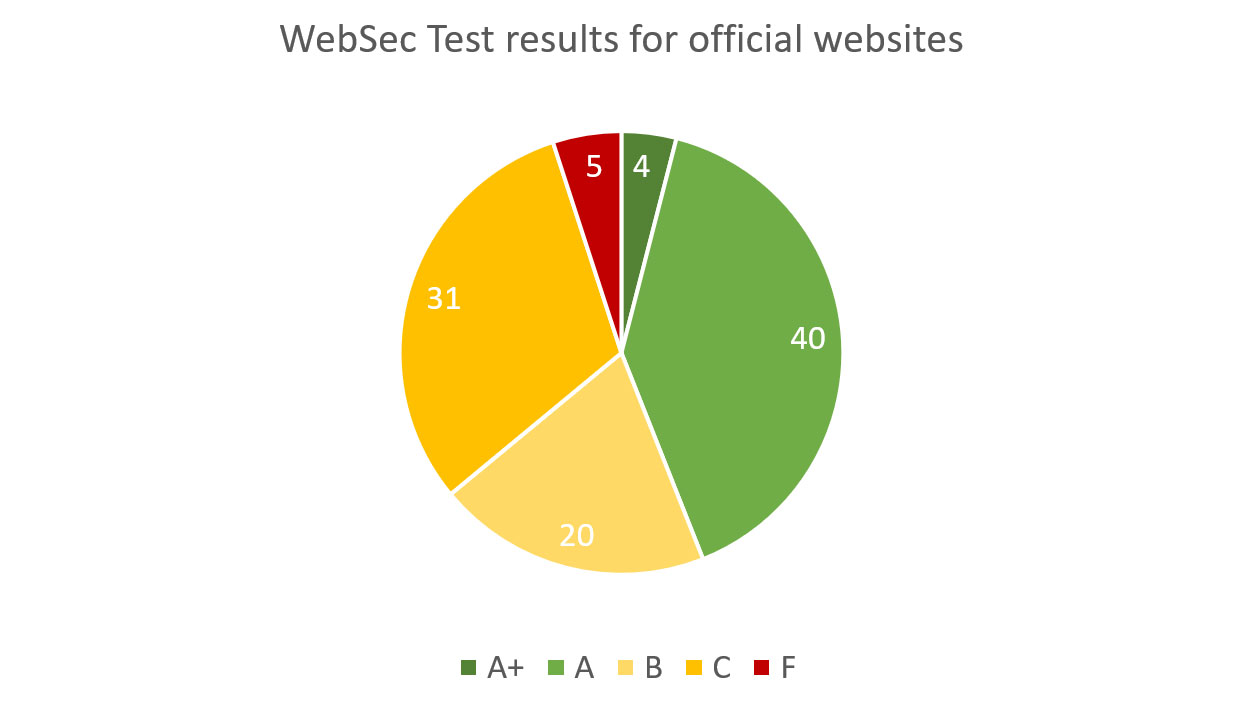
Diagram 2: Website Security of Main Websites
| Grade | Quantity | Brief explanation (see above for detailed methodology) |
|---|---|---|
| A+ | 4 | No single issue or misconfiguration found |
| A | 40 | Minuscule issues found or slightly insufficient security hardening |
| B | 20 | Several minor issues or insufficient security hardening |
| C | 31 | Security vulnerabilities or several serious misconfigurations found |
| F | 5 | Exploitable and publicly known security vulnerabilities found |
Below are website security grades for the subdomains:
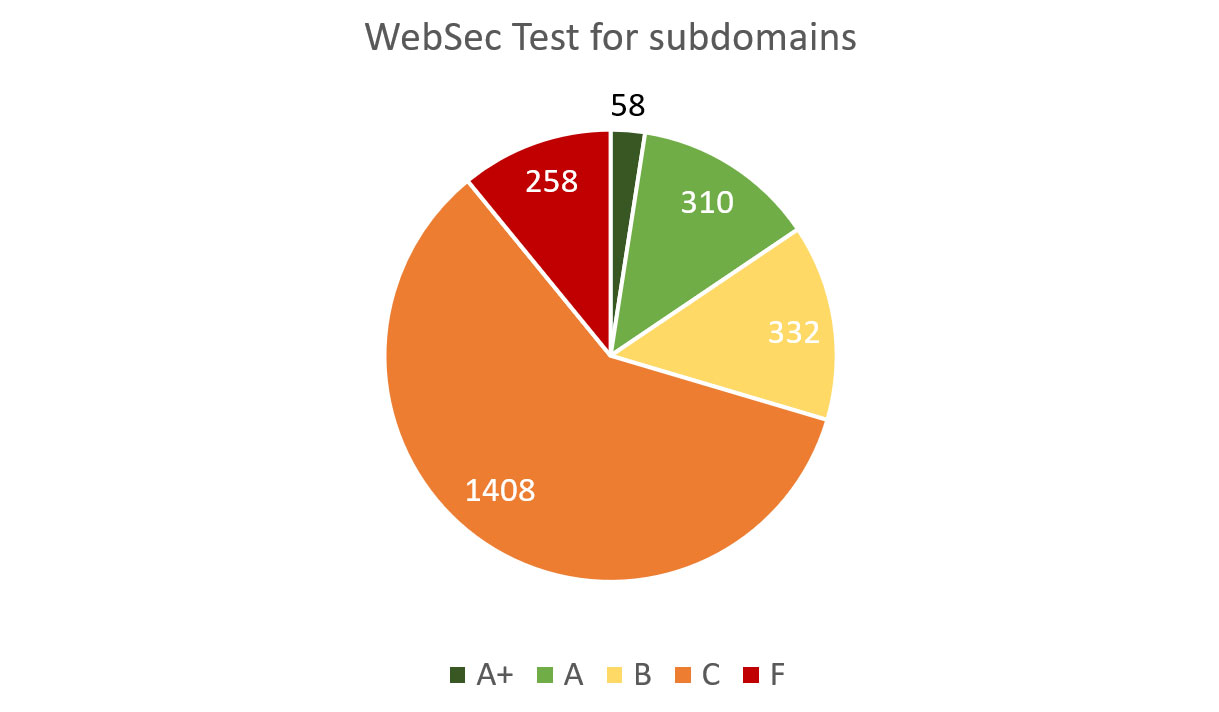
Diagram 3: Website Security of Subdomains
| Grade | Quantity | Brief explanation (see above for detailed methodology) |
|---|---|---|
| A+ | 58 | No single issue or misconfiguration found |
| A | 310 | Minuscule issues found or slightly insufficient security hardening |
| B | 332 | Several minor issues or insufficient security hardening |
| C | 1408 | Security vulnerabilities or several serious misconfigurations found |
| F | 258 | Exploitable and publicly known security vulnerabilities found |
Below are website security grades for the e-banking web applications:
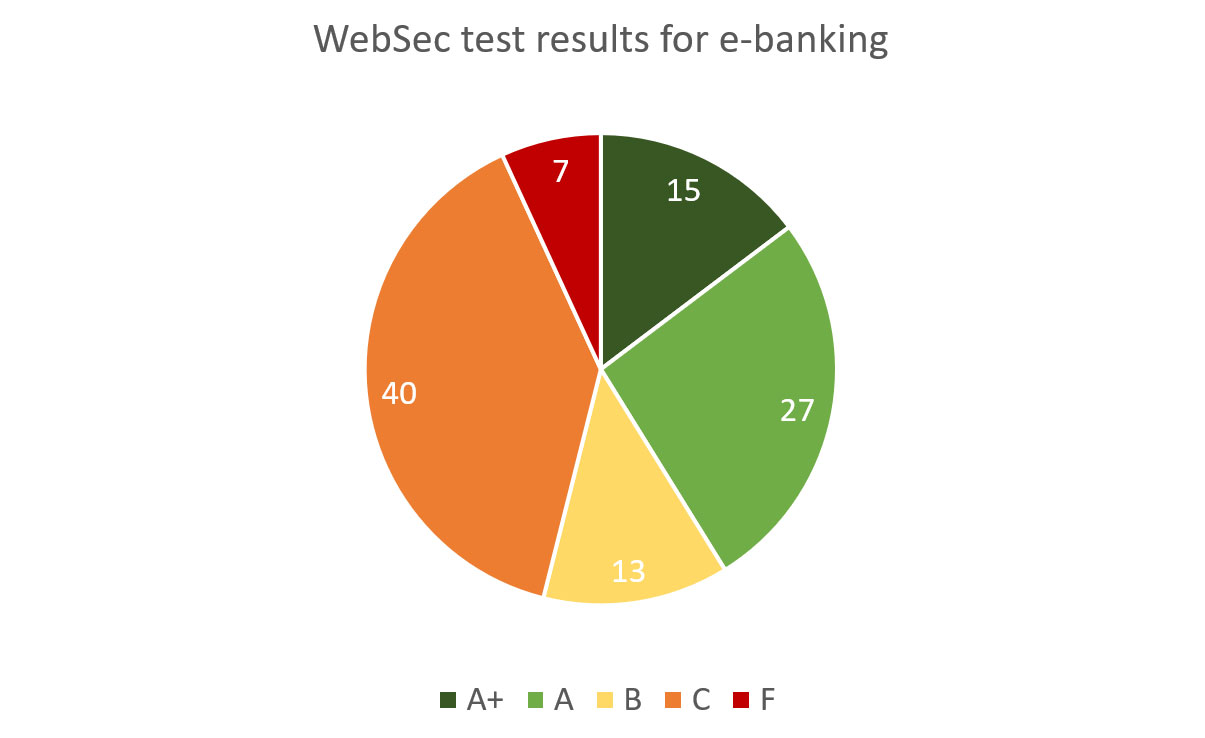
Diagram 4: Website Security of E-Banking
| Grade | Quantity | Brief explanation (see above for detailed methodology) |
|---|---|---|
| A+ | 15 | No single issue or misconfiguration found |
| A | 27 | Minuscule issues found or slightly insufficient security hardening |
| B | 13 | Several minor issues or insufficient security hardening |
| C | 40 | Security vulnerabilities or several serious misconfigurations found |
| F | 7 | Exploitable and publicly known security vulnerabilities found |
SSL/TLS Encryption Security
Below are SSL/TLS encryption security grades for the main websites:
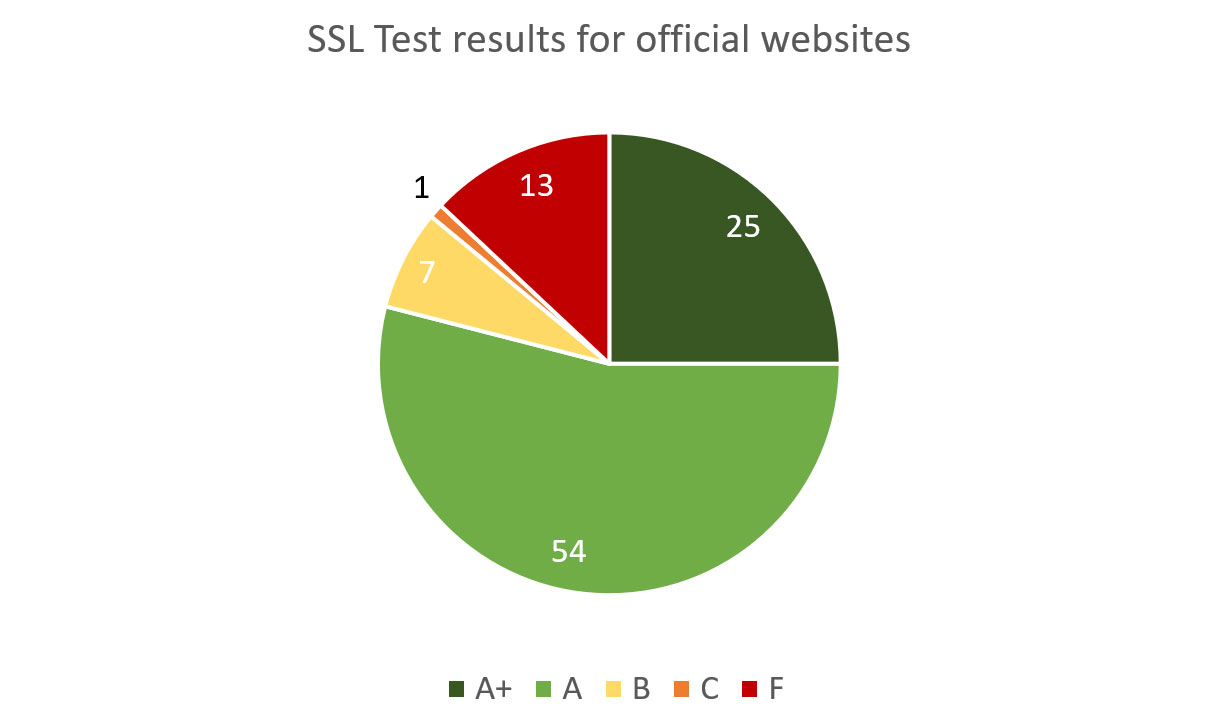
Diagram 5: SSL Security of Main Websites
| Grade | Quantity | Brief explanation (see above for detailed methodology) |
|---|---|---|
| A+ | 25 | No single issue or misconfiguration found |
| A | 54 | Minuscule issues found or slightly insufficient encryption hardening |
| B | 7 | Several minor issues or insufficient encryption hardening |
| C | 1 | Security vulnerabilities or several serious misconfigurations found |
| F | 13 | No encryption, SSLv3 or exploitable security vulnerabilities found |
Below are SSL/TLS encryption security grades for the subdomains:
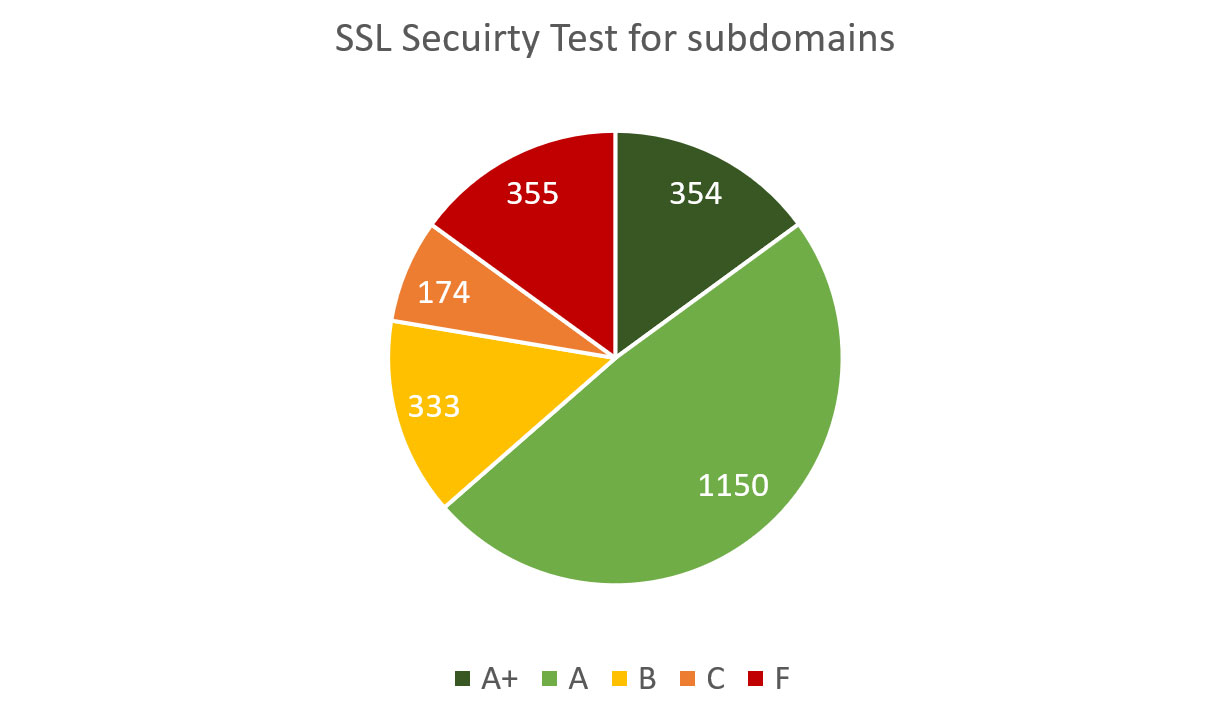
Diagram 6: SSL Security of Subdomains
| Grade | Quantity | Brief explanation (see above for detailed methodology) |
|---|---|---|
| A+ | 354 | No single issue or misconfiguration found |
| A | 1150 | Minuscule issues found or slightly insufficient encryption hardening |
| B | 333 | Several minor issues or insufficient encryption hardening |
| C | 174 | Security vulnerabilities or several serious misconfigurations found |
| F | 355 | No encryption, SSLv3 or exploitable security vulnerabilities found |
Below are SSL/TLS encryption security grades for the e-banking web applications:
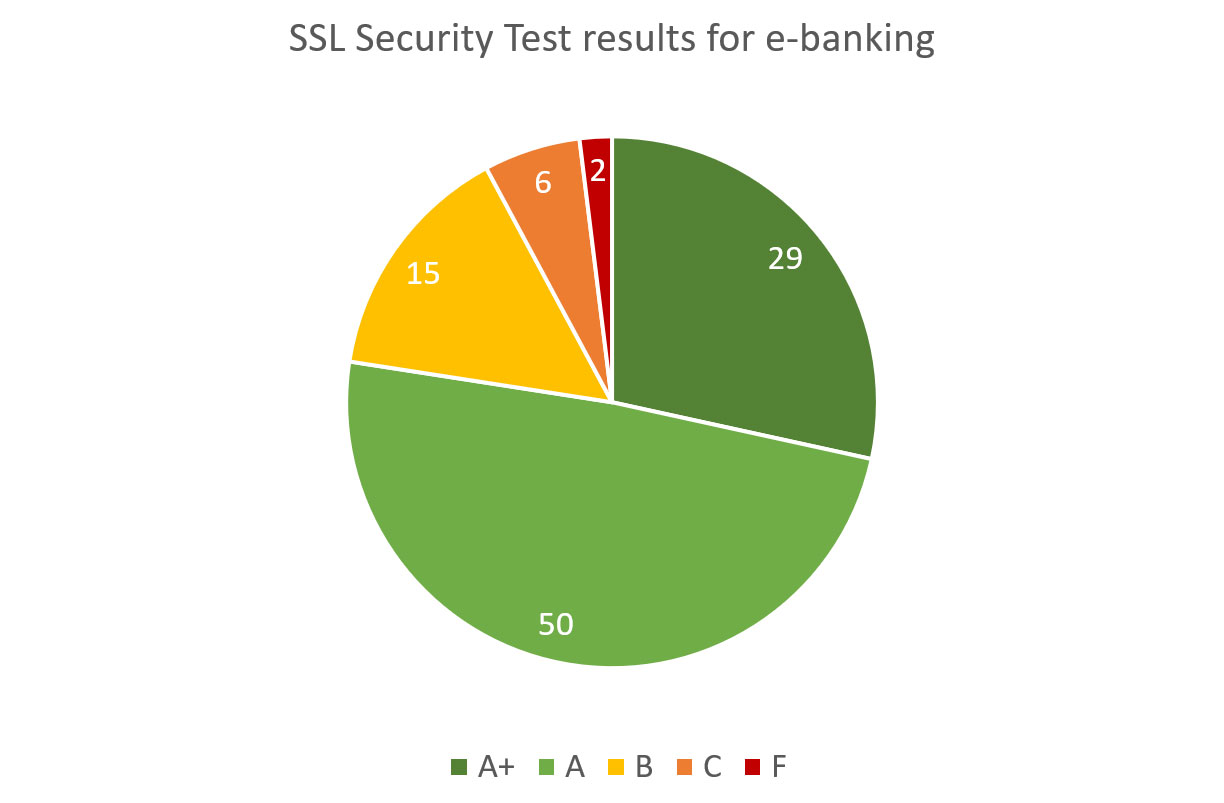
Diagram 7: SSL Security of E-Banking
| Grade | Quantity | Brief explanation (see above for detailed methodology) |
|---|---|---|
| A+ | 29 | No single issue or misconfiguration found |
| A | 50 | Minuscule issues found or slightly insufficient encryption hardening |
| B | 15 | Several minor issues or insufficient encryption hardening |
| C | 6 | Security vulnerabilities or several serious misconfigurations found |
| F | 2 | No encryption, SSLv3 or exploitable security vulnerabilities found |
PCI DSS and GDPR Website Compliance
Below are PCI DSS compliance tests for the main websites:
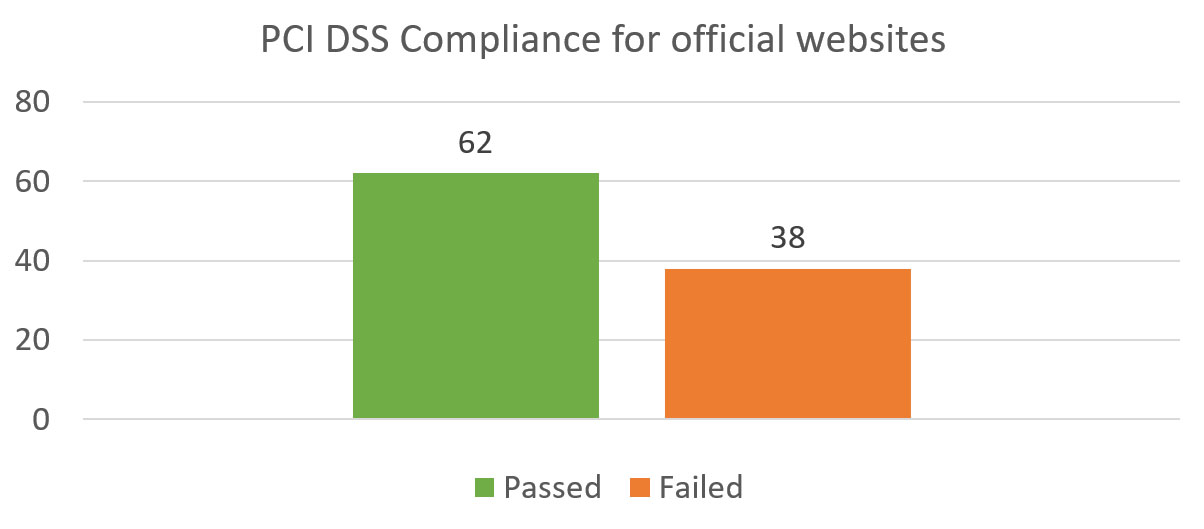
Diagram 8: PCI Compliance of Main Websites
Below are PCI DSS compliance tests for the subdomains:
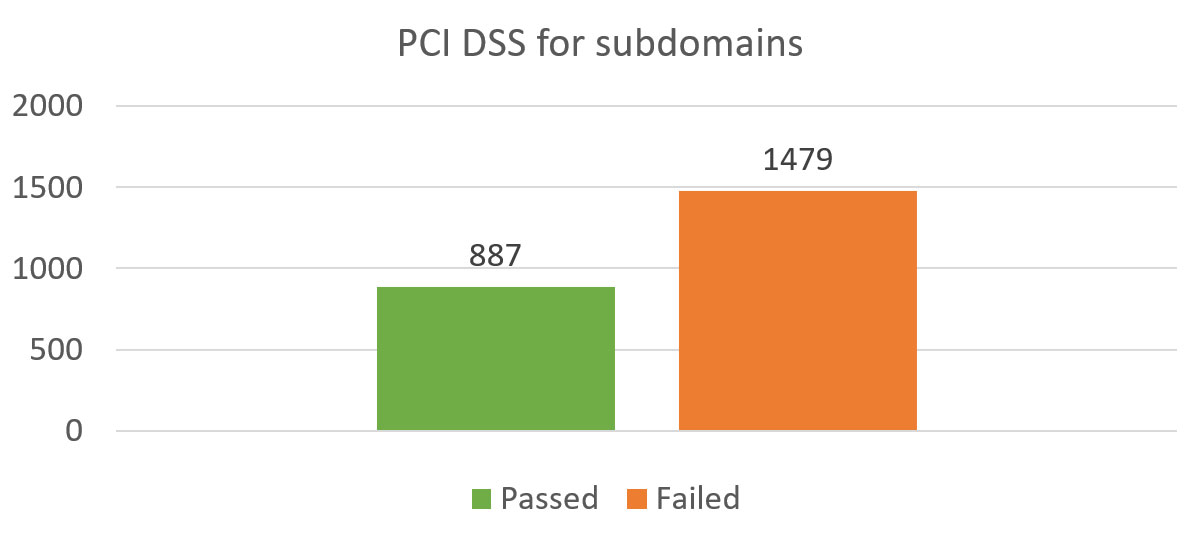
Diagram 9: PCI Compliance of Subdomains
Below are PCI DSS compliance tests for the e-banking web applications:
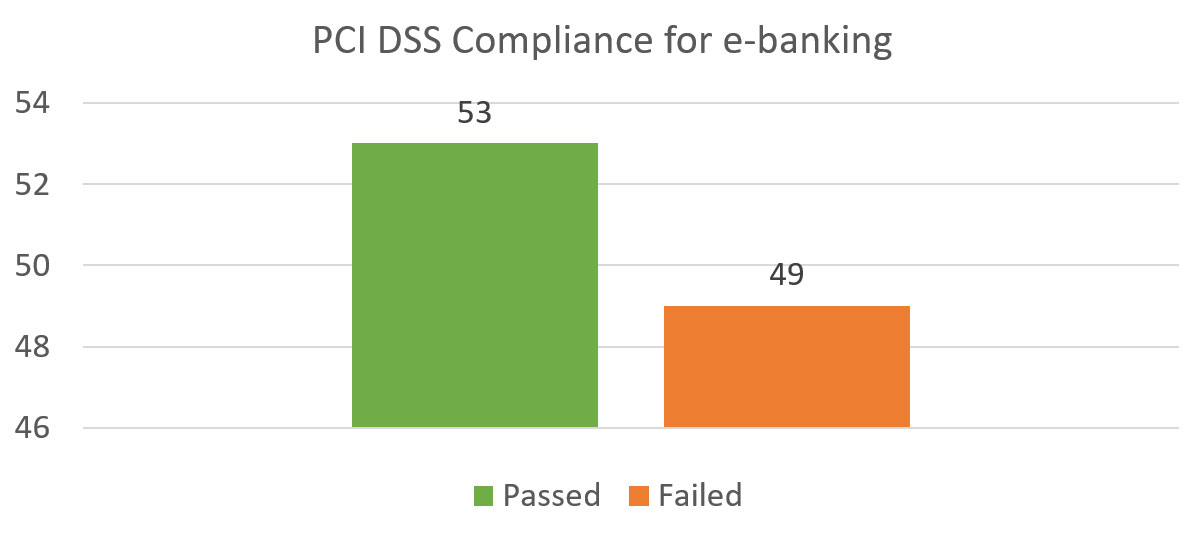
Diagram 10: PCI Compliance of E-Banking
Below are GDPR compliance tests for the main websites:
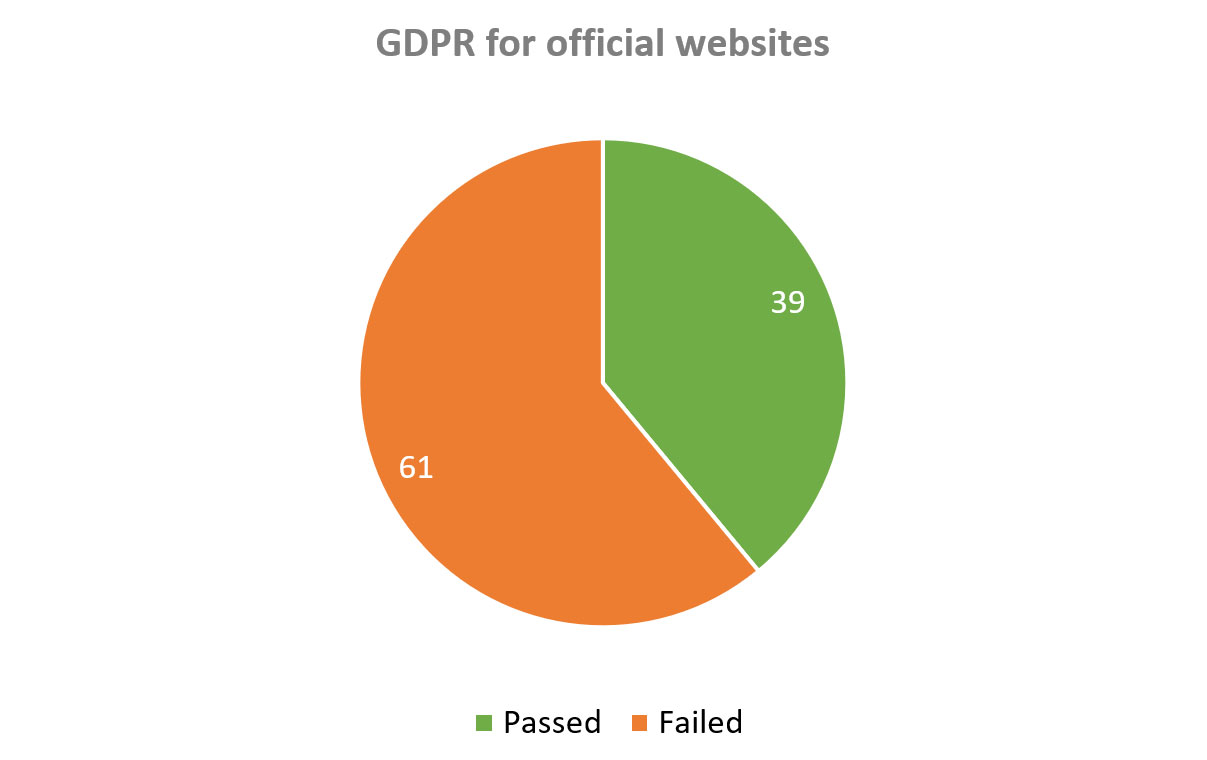
Diagram 11: GDPR Compliance of Main Websites
Below are GDPR compliance tests for the subdomains:
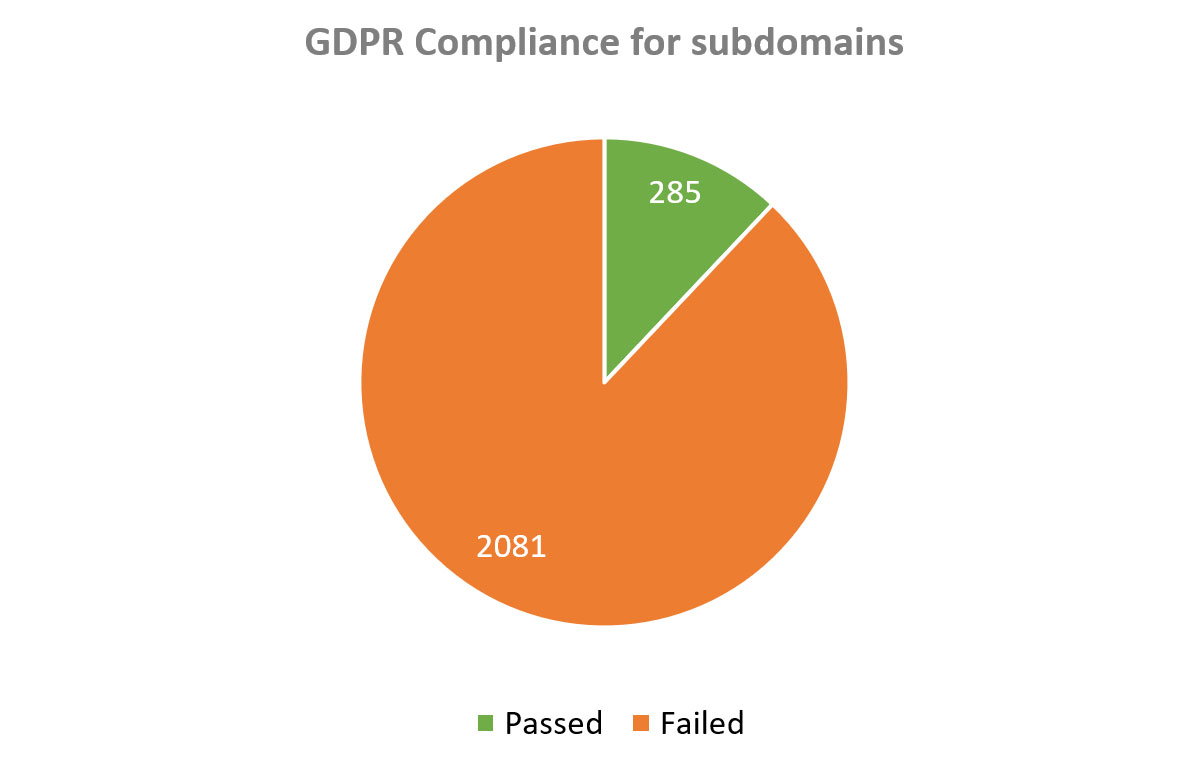
Diagram 12: GDPR Compliance of Subdomains
Below are GDPR compliance tests for the e-banking web applications:
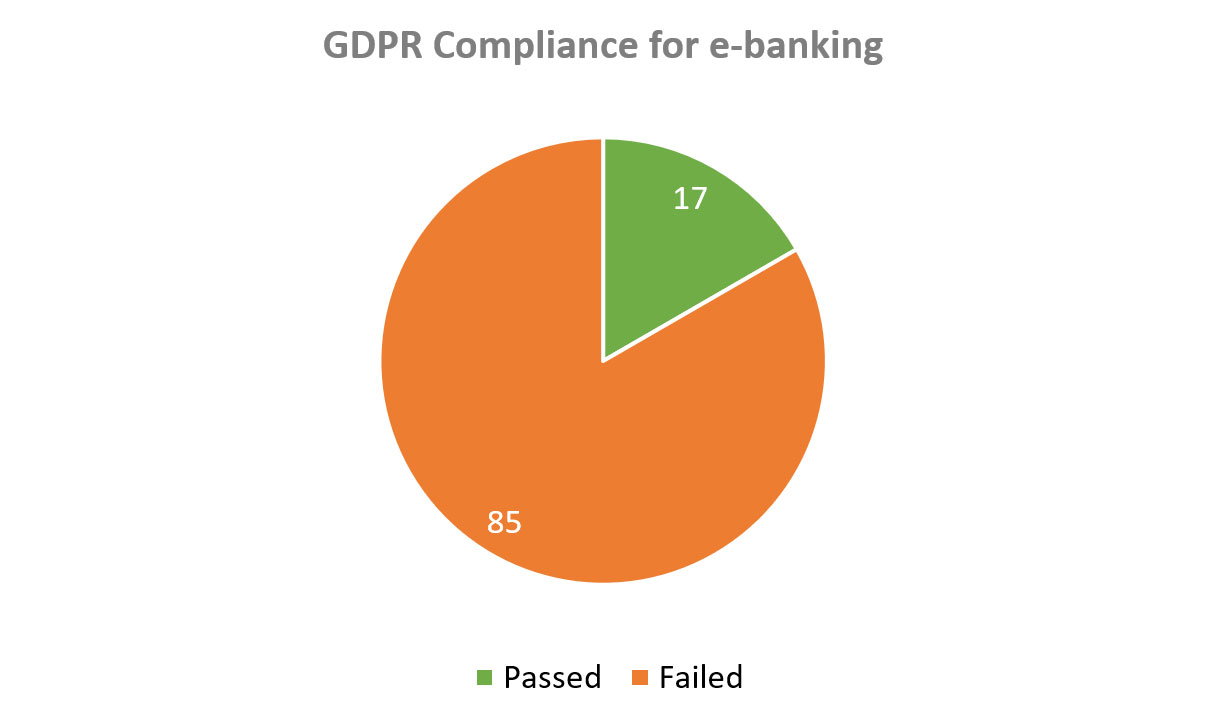
Diagram 13: GDPR Compliance of E-Banking
Outdated and Vulnerable Web Software
Modern websites leverage peculiar combinations of open source and proprietary web frameworks and other software to improve performance, tracking or SEO.
A rapidly growing volume of web software from different and frequently ephemeral vendors leads to growing risks that impact even the main (“www.”) websites of the banks:
- On average, each website contains 2 different web software components, JS libraries, frameworks or other third-party code.
- As many as 29 websites contain at least one publicly disclosed and unpatched security vulnerability of a medium or high-risk.
- The oldest unpatched vulnerability detected during the research is CVE-2011-4969 impacting jQuery 1.6.1 and known since 2011.
- Most popular website vulnerabilities were XSS (Cross Site Scripting, OWASP A7), Sensitive Data Exposure (OWASP A3) and Security Misconfiguration (OWASP A6).
With regard to the subdomains, the situation is even more disastrous with outdated components:
- 81% of the subdomains that contain fingerprintable external software have outdated components
- 2% contain publicly disclosed and exploitable vulnerability of medium or high risk
Furthermore, a nonprofit Open Bug Bounty project contains 147 XSS vulnerability reports affecting websites of the banks from this research. 28 publicly disclosed vulnerabilities remain unpatched, with 5 vulnerabilities reported and unpatched for over 2 years.
Usage of Web Application Firewalls
Gartner forecasts that the Web Application Firewall (WAF) market will total $853 million in 2018, which is an increase of 11.9% from 2017’s total of $762 million.
At a glance, WAF usage in the banking sector is indeed quite widespread. As few as 8 banks seem not to use an external WAF for their main website or use a WAF in a permissive monitoring-only mode thus not blocking any web attacks in real time.
However, for the e-banking websites the problem proliferates across as many as 25 financial institutions. This can be possibly explained by irking false-positives when a WAF erroneously blocks a legitimate user for an unusual HTTP request or behavioral pattern. This creates an important business problem of disgruntled customers who are get locked out from their e-banking interface while conducting an important money transfer or checking their account balance.
For subdomains statistics is even more worrisome with 47% of unprotected web applications. Frequently, subdomains serve a good, albeit notorious, example of abandoned, forgotten, legacy or shadow applications that for a reason are not included into the scope of cyberdefense perimeter and are in fact a low-hanging fruit for the attackers. ImmuniWeb Discovery can rapidly illuminate and rate security risks of your external attack surface.
Mobile Banking Applications
During the research we tested 55 mobile banking applications allowing access to sensitive banking data. In total, these mobile apps communicated with 298 backend APIs to send or receive data from the bank.
All of the mobile apps were tested for Mobile OWASP Top 10 security and privacy issues. Given a very sensitive nature of the banking data handled by the mobile banking applications, which are regularly tested by numerous solutions and security services providers, we find below-mentioned statistics quite disturbing:
- 100% of mobile banking applications contain at least 1 low-risk security vulnerability
- 92% of mobile banking applications contain at least 1 medium-risk security vulnerability
- 20% of mobile banking applications contain at least 1 high-risk security vulnerability
Three most common OWASP Mobile Top 10 security issues are:
- M1: Improper Platform Usage
- M2: Insecure Data Storage
- M7: Client Code Quality
Mobile applications’ backends are usually a REST or SOAP APIs not designed to interact with users via a web browser but rather to receive HTTP/S requests from mobile app or other software. Consequently, we did not run here inapplicable website security tests but SSL encryption test to verify how the transmitted data is encrypted. Most of the backend APIs have strong SSL/TLS encryption and its implementation:
- 198 received an “A” grade
- 44 got the highest “A+” grade
However, as much as 18 were scored with a failing “F” grade meaning that communications can be easily intercepted due to known and exploitable cryptographic or SSL/TLS implementation vulnerabilities:
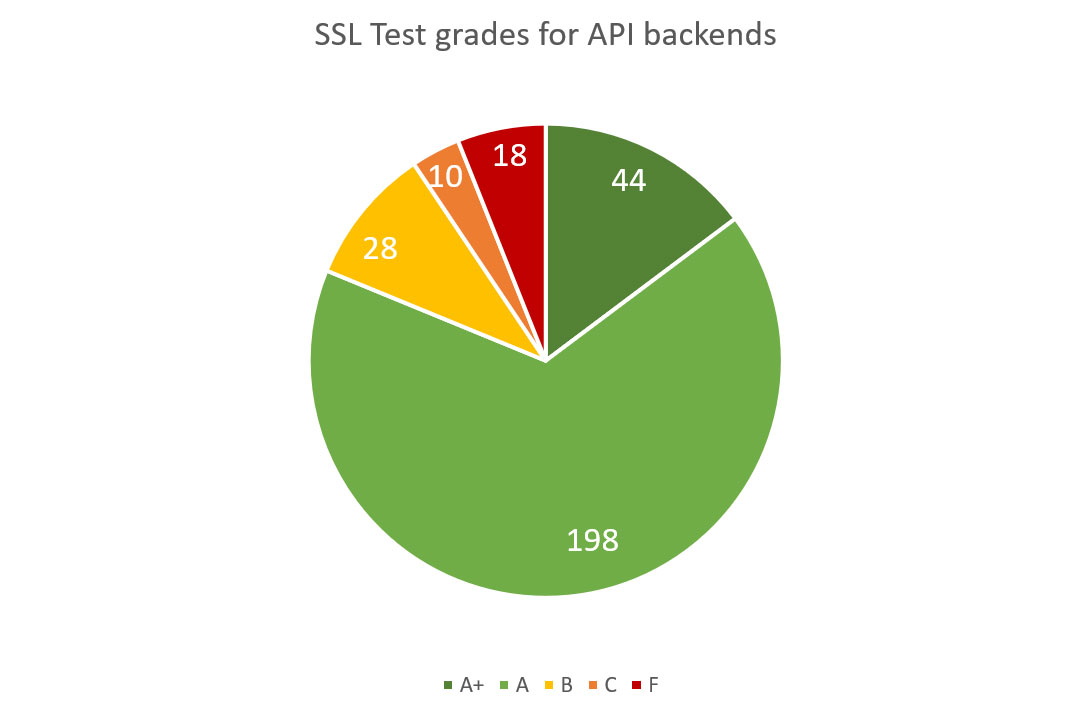
Diagram 14: SSL Security of Mobile Backend APIs
Phishing Campaigns
We detected 29 active phishing campaigns targeting customers of the financial institutions. The most targeted banks are depicted below:
| Website | Active Phishing Campaigns | Total Phishing Campaigns |
|---|---|---|
| jpmorganchase.com | 3 | 227 |
| bankofamerica.com | 8 | 179 |
| wellsfargo.com | 7 | 185 |
Phishing websites either spread banking malware aimed to steal e-banking credentials or provide fraudulent login forms aimed to steal victim’s credentials.
Most of the malicious websites were hosted in the US.
Trademark Infringement and Domain Squatting
We detected about 6500 cybersquatted domains of illicit, fraudulent or potentially deceptive nature. Below is an example of newly registered domains alleging a connection to Wells Fargo:
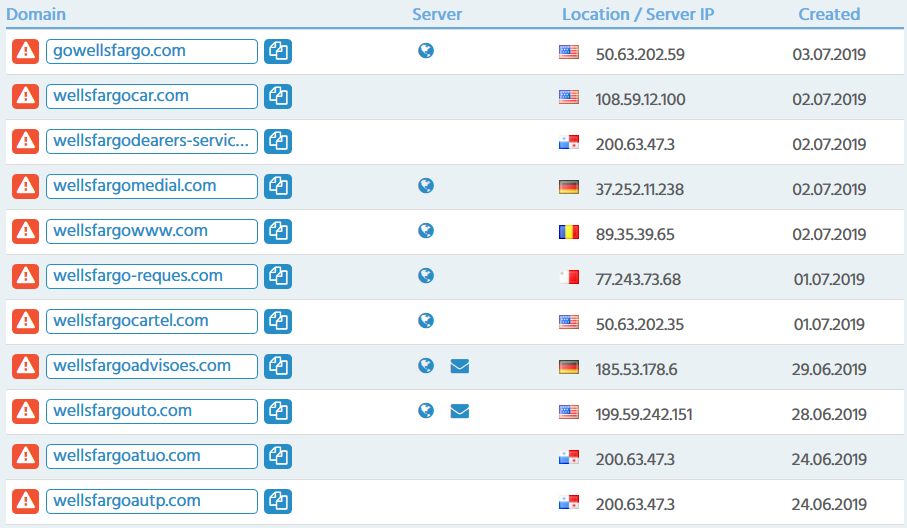
Over 32% of cybersquatting websites are accessible via HTTPS connection with a valid SSL certificate. Most popular Certificate Authorities (CA) are:
- Google Internet Authority G3 (47%)
- COMODO RSA Domain Validation Secure Server CA (26%)
- Let's Encrypt Authority X3 (9.7%)
Over 80% of all squatted domains had at least one website, related to Bitcoin or other cryptocurrencies.
Brand misuse also happens in social networks, mostly in Facebook and Twitter. During the research, we also identified over 160 squatted pages in these two social networks designed to mislead users or offer fake service on behalf of legitimate banks.
Typosquatting is usually less dangerous than cybersquatting and mostly targets unfair theft of web traffic when brand users mistype the URL in their browser. We detected more than 1300 domains with common typos squatted by third-parties for various, often illicit, purposes:
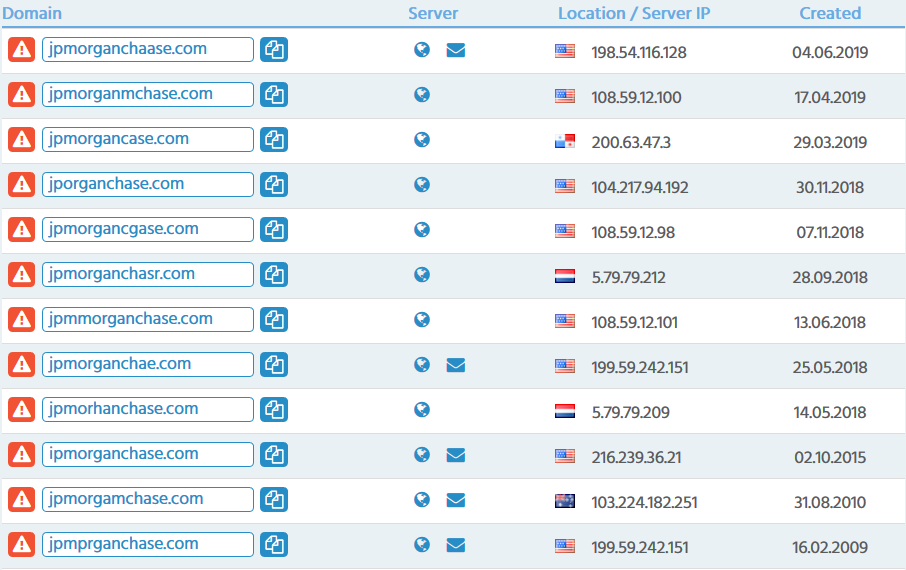
Over 4% of typosquatting websites are accessible via HTTPS connection with a valid SSL certificate. Most popular Certificate Authorities (CA) here are:
- Let's Encrypt Authority X3 (77%)
- DigiCert SHA2 High Assurance Server CA (8%)
- Go Daddy Secure Certificate Authority (2%)
Frequently typosquatted domains redirect inattentive users to various doorways and then, depending on the victim’s geo location, device type or language, forward the victim to websites with adult-oriented or illicit trade content.
Above 30% of the destination websites contained known malware or spyware detectable by Virus Total.
Recommendations
Ilia Kolochenko, CEO and Founder of ImmuniWeb, says: “Given the non-intrusive methodology of our research, as well as important financial resources available to the banks, the findings urge financial institutions to rapidly revise and enhance their existing approaches to application security. Nowadays, most of the data breaches involve insecure web or mobile apps, importance of which is frequently underestimated by the future victims. Recent BA’s £183 million fine for a website databreach clearly illustrates the point.
Today, in light of the growing shortage of cybersecurity skills, most security teams carry a burdensome duty to meet tough compliance and regulatory requirements as their first priority, often giving up other essential tasks and processes. Application security frequently suffers a lot as a result. Eventually, these companies become a low-hanging fruit for pragmatic and profit-oriented cybercriminals.”
ImmuniWeb suggests four recommendations to avoid most of the problems described above:
1. Consider implementing Gartner’s CARTA strategy to enhance your cybersecurity strategy.
2. Maintain a holistic and up2date inventory of assets located in your external attack surface, identify all software and its components used there, run actionable security scoring on it to enable threat-aware and risk-based remediation.
3. Implement continuous security monitoring of your external attack surface, test your new code before and after deployment to production, start implementing DevSecOps approach to your application security.
4. Consider leveraging Machine Learning and AI capacities to handle time-consuming and routine processes, freeing up your security personnel for more important tasks, suggested reading: “4 Practical Questions to Ask Before Investing in AI”.
Need further help or expert advice? Request a free trial now or get in touch!


