Cyber Security Compliance
Сyber security compliance has become one of the most important aspects of any company's life. Businesses are actively considering the best practices and concepts for cyber security, that would help solve tasks related to risk management.

The Internet is constantly evolving and expanding thus improving the quality of interaction among people and companies around the world. With the spread of public open Wi-Fi networks, we got the possibility to be in touch almost always and everywhere, but such openness requires increased attention to cyber security compliance, since devices connected to open networks can be vulnerable.
Why Cyber Security Compliance Is a Must

Cyber security is a prerequisite for the development of the information society. The target for a cyber attack can be both individuals and businesses with money or data that can be of any value. For businesses, protecting information is just as important as for governments protecting their secrets.
Want to have an in-depth understanding of all modern aspects of Cyber Security Compliance? Read carefully this article and bookmark it to get back later, we regularly update this page.
It doesn’t matter what type of business your company is engaged in - technological, banking, medical or fast food services, if you sell something, then a lot of personal data is stored in your network. Your business’s digital assets need protection around the clock no less than physical assets or bank deposits.
Recent research by ImmuniWeb shows that millions of stolen corporate credentials are available in the Dark Web and exploited by cybercriminals for spear-phishing and password re-use attacks against the largest global companies.
Therefore, cyber security compliance is especially important for companies, since both ordinary thieves and dishonest competitors who resort to hacker services can take advantage of vulnerabilities.
In addition to the dangers to your business and company assets all companies must use cyber security and confidentiality compliance mechanisms when collecting or processing user personal information to comply with various regulations. For example, the EU's General Data Protection Regulation or GDPR which came into force just less than 2 years ago has already become a nightmare for European business owners. See the statistics of GDPR breaches in the following graph.
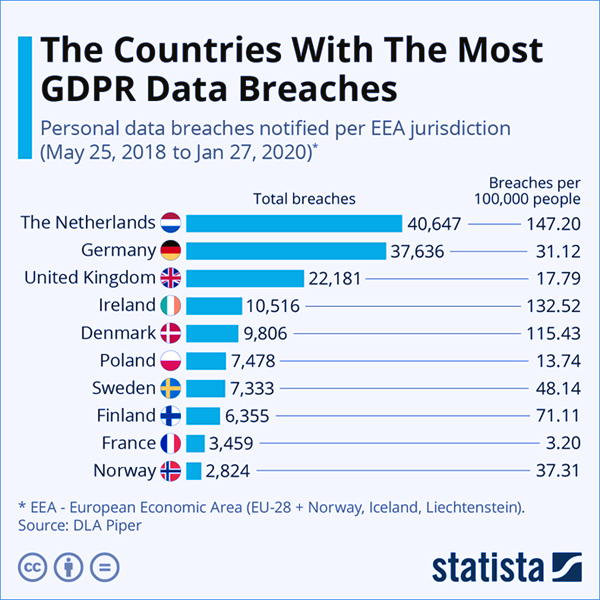 The Countries with the Most GDPR Data Breaches Source: Statista.com
The Countries with the Most GDPR Data Breaches Source: Statista.com ImmuniWeb can help your organization meet emerging cyber security compliance requirements such as GDPR, PCIDSS, and many others in a simple, agile, and cost-effective manner.
GDPR is not the only regulation. Such compliances and regulations are adopted in many countries all over the world. And in order to meet all these requirements you should enforce you cyber security compliance. Here are the most common ways to do it.
Enforce Cyber Security Compliance

1. Be careful what you publish
Enforcing your company's cyber security compliance begins with personal information security. Watch and carefully filter what information you disseminate on the Internet about yourself and your company. By sharing the "wrong" information, you can attract the attention of criminals of all stripes and become vulnerable to theft or hacking. Attackers can track what you say on the Internet in your social nets and use it to their own advantage. Do disclose any information about yourself, your brand, your colleges, your products, unless you are absolutely sure that it will not be used against you.
2. Make sure that the data your company collects is well protected
In order to keep your business data safe, you should conduct an audit and determine which of it is public information and do not require careful protection, which data is of medium importance and its leakage will not affect the business much, and at the end which data is the most important and confidential. The latter category of data will greatly affect the business in case of theft, so it needs to be protected as reliably as possible with the most strict access rights for employees and partners.
3. Enable HTTPS for your website
To activate HTTPS, an SSL / TLS certificate is installed on the server. This certificate encrypts all data between the browser and the server, whether it’s personal or financial information that is entered on the web page, or the contents of the pages. So the information is protected from third parties, for example, intruders or surveillance.
SSL certificates can also link your brand to a website This allows visitors to make sure that your website really belongs to your company, but not to a scammer in the case of a phishing site. The EV SSL certificate clearly demonstrates this by coloring the address bar of the browser in green and showing the name of your company.
Use the opportunity to test SSL for free to ensure your cyber security.
4. Use strong and unique passwords
Many Dark Web hackers sell the data that they managed to obtain, including information about millions of users and their passwords. Do not use the same password on different accounts. It vastly increases chances to be hacked. Hackers can pick up your passwords using brute force. It is much more difficult if the password is long, composed of various characters and does not contain words from the dictionary. Use some password manager to remember unique passwords for each service.
5. Use several authentication factors
Authentication is the act of verifying the identity of a user or device before allowing access to the system. This is done by comparing the provided credentials with an existing database of authorized users, for example, entering a username and password to access an email account. But instead of relying solely on passwords, which are becoming increasingly insecure, we recommend using several factors authentication. Among these factors, a user's specific secret, for example, the answer to a secret question, a digital certificate, a smart card, or a biometric data, such as a fingerprint.
6. Update all software
Hackers are always looking for new vulnerabilities in the software that you use. Finding them is as easy as finding a path on your Windows network. At the same time, software companies themselves are working hard to release patches to fix these vulnerabilities, so it is very important to update the software as soon as the update is released.
7. Back up all data
Backups ensure that in case of data loss, files can be restored. You should always store data in different locations physically spaced to ensure cyber security compliance, since hackers will not be able to access everything at once. Remember that backups need to be updated regularly.
8. Install a firewall on the Internet gateway
Firewalls are designed to prevent unauthorized access to a private network. You can establish a set of rules to determine which traffic is allowed and which is prohibited. A good firewall should monitor both inbound and outbound traffic.
ImmuniWeb® Discovery reduces complexity and costs of cyber security compliance via continuous discovery of your external digital assets and attack surface enhanced with proactive Dark Web monitoring.
Use Basic Cyber Security Compliance Rules in Your Company

Typically, recommendations on cyber security compliance for companies are prescribed and mandatory for acknowledging and implementation by employees of the organization who use devices with the ability to access the Internet. The list of these rules may vary slightly depending on the company, but often it consists of several basic recommendations to keep the cyber security of the company at a high level:
- the use of complex passwords with their regular change;
- a ban on opening and launching unknown files;
- a ban on downloading and installing new software for the implementation of which they use an admin password on all devices on the corporate network;
- a ban on opening e-mail from unknown and suspicious addresses;
- private access to internal files of the system, using exclusively corporate mail to transfer access to them;
- limited user access to projects of a different level. Each employee has access exclusively to the projects that he or she needs to work;
- a ban on the use of removable digital storage devices;
- use of licensed software.
These measures are basic, but when implemented, are sufficiently effective to ensure the cyber security compliance of the company. Of course, they themselves do not protect against hacker attacks on the company’s network, but they leave much less chances for their successful conduct.
You can check your website right now for GDPR and PCIDSS compliance using ImmuniWeb Website Security Free Test.
Additional Resources
- Learn more about AI-enabled Attack Surface Management with ImmuniWeb® Discovery
- Learn more about AI-enabled Application Penetration Testing with ImmuniWeb
- Learn more about ImmuniWeb Partner Program opportunities
- Follow ImmuniWeb on Twitter and LinkedIn

