Singapore Releases New Cybersecurity Guidelines to Combat COVID-19 Threats
The Monetary Authority of Singapore (MAS) has issued a set of recommendations addressing Open Source Software security and TPRM program to keep your business secure amid the pandemic.

Last week, the Monetary Authority of Singapore (MAS)'s Cyber Security Advisory Panel (CSAP) stressed the need for financial institutions (FIs) to review their security controls given the elevated technology-related risks arising from remote working and safe management measures due to the COVID-19 pandemic.
The key recommendations from the CSAP meeting include the following:
- Maintaining oversight of third-party vendors and their controls. With the increased reliance on third-party vendors, the Panel emphasized the need for FIs to step up their oversight of these counterparts and to monitor and secure remote access by third-parties to FIs’ systems. This is even more important during the COVID-19 pandemic where remote working has become pervasive.
- Strengthening governance over the use of open-source software (OSS). Vulnerabilities in OSS are typically targeted and exploited by threat actors. The Panel recommended that FIs establish policies and procedures on the use of OSS and to ensure these codes are robustly reviewed and tested before they are deployed in the FIs’ IT environment.
The recommendations are in perfect harmony with the development of other cybersecurity regulations around the globe. For instance, financial institutions and other entities covered by the 23 NYCRR 500, developed by the New York State Department of Financial Services (NYSDFS), must implement a sound Third-Party Risk Management Program (TPRM) under the “500.11 Third-party service provider security policy” section of the state law.
Similarly, SEC’s Office of Compliance Inspection and Examination (OCIE) recently pointed out in its cybersecurity guidelines (part of the Regulation S-P) that “Registrants failed to follow their own policies and procedures regarding outside vendors” and suggested to pay more attention to third-party risks.
At ImmuniWeb, we can help addressing both requirements in a simple and cost-efficient manner with our flagship ImmuniWeb Discovery. This OSINT-based solution is non-intrusive and production-safe, and thus can be leveraged to assess your own cybersecurity as well to scorecard your trusted third-parties. All you need to visualize external attack surface and Dark Web exposure of a company is to enter the company name:
Creating ImmuniWeb Discovery Project
In a couple of days, you will get the interactive dashboard with easily consumable information about your external IT assets, spanning from APIs and mobile apps endpoints to exposed VPN servers, IoT devices and unprotected public cloud storage.
All the assets will be classified and risk-scored, accompanied with compliance tests where applicable, while all external web applications will have inclusive list of Open Source and proprietary software with fingerprinted versions and known security vulnerabilities:
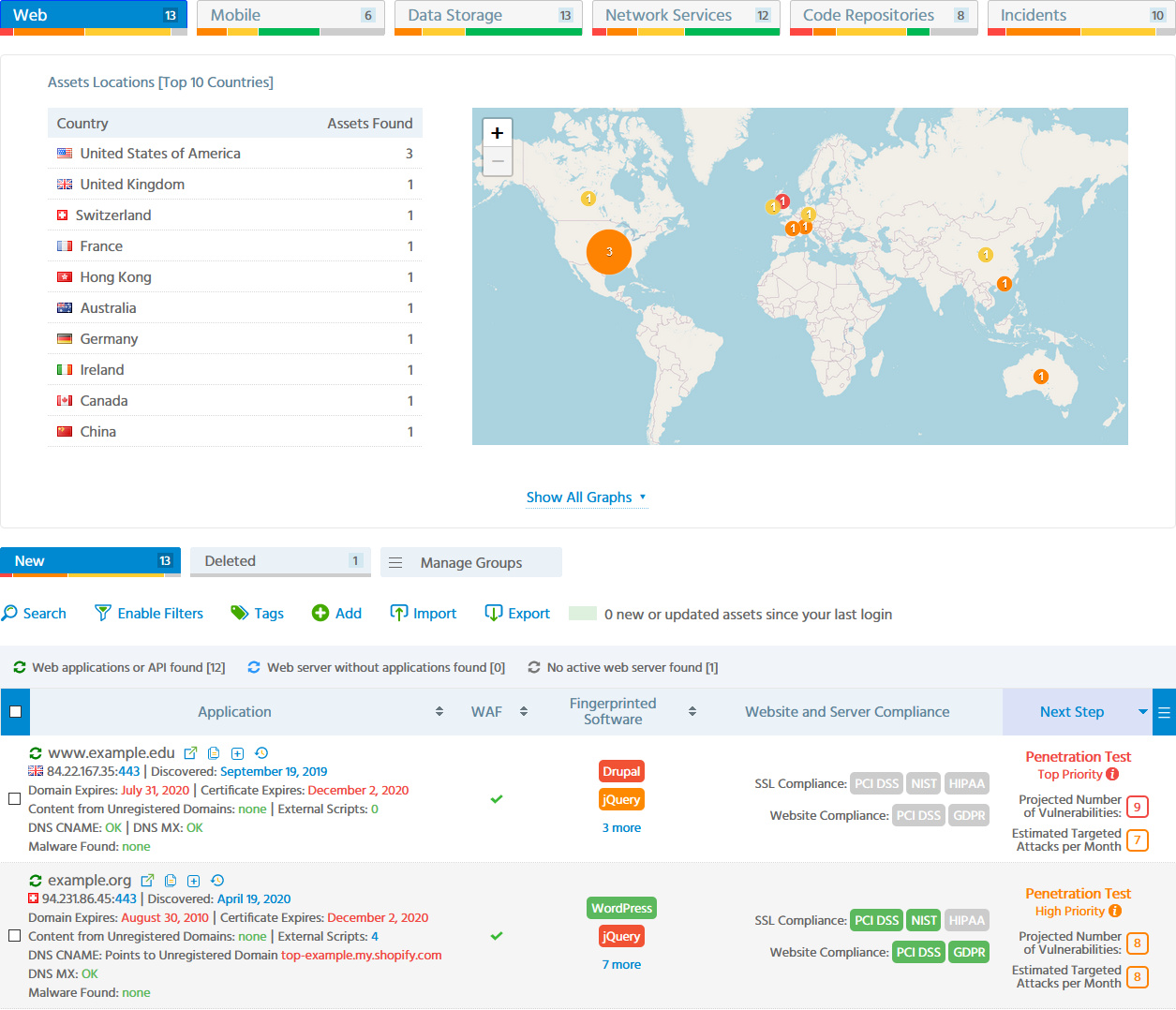
Application inventory with Software Composition Analysis (SCA)
On top of this, you will see a detailed snapshot of company’s Dark Web exposure and security incidents in the Surface Web such as phishing, domain squatting, fake accounts in social networks, or presence of Indicator of Compromise (IoC) among the assets:
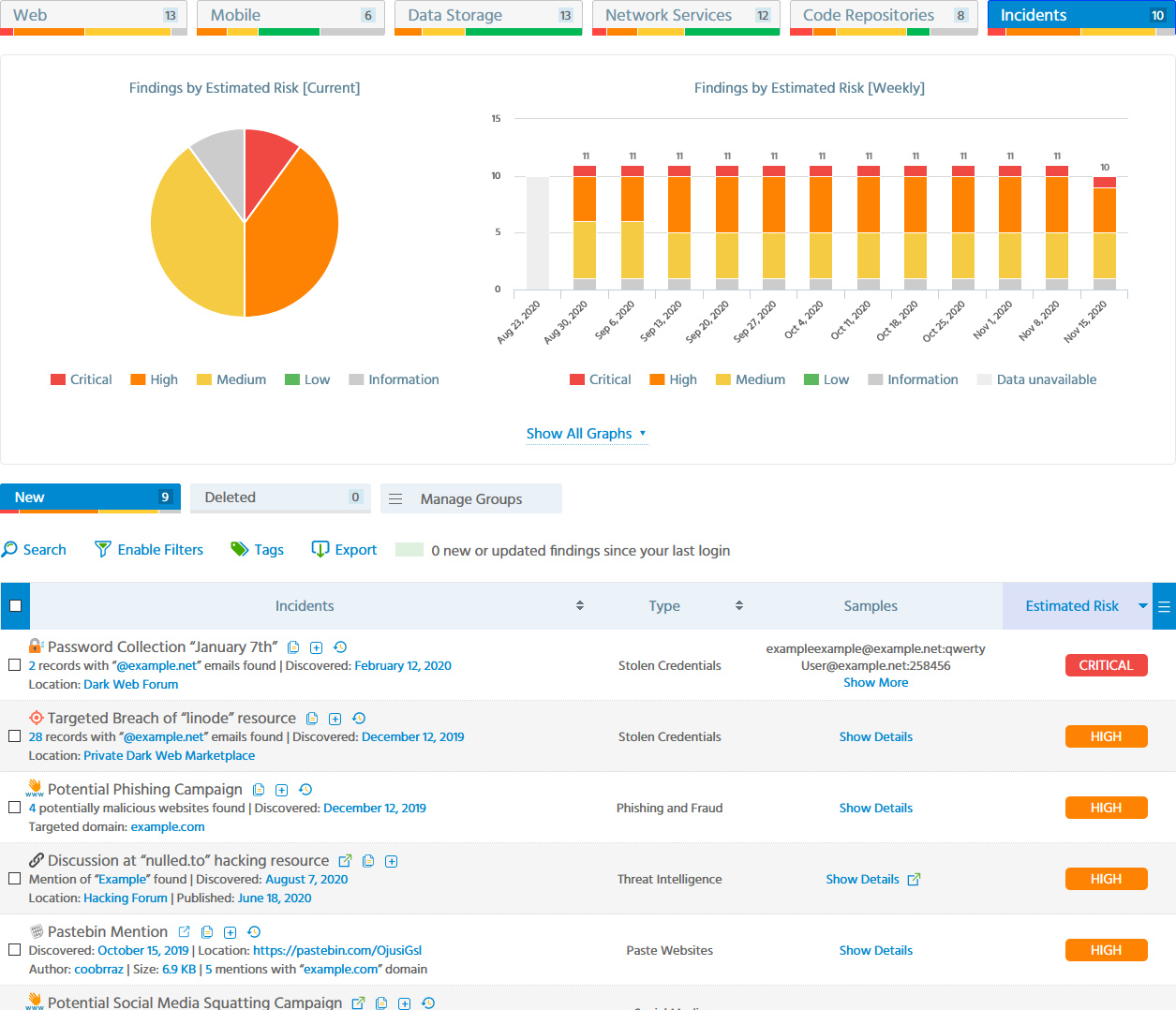
Security incidents and Dark Web monitoring
Packaging is per company, with no limit of discoverable assets or searchable incidents, so you don’t need to bother about any fluctuation in the number of assets or security incidents.
As detailed above, ImmuniWeb Discovery can now easily help meeting the new guidelines of MAS in Singapore, provide you with a continuous assurance of your own cybersecurity, and enable you to keep an eye on your trusted third-parties in a simple and holistic manner.




