State of Cybersecurity at Top 100 Global Airports
97 out of 100 of the world's largest airports have security risks related to vulnerable web and mobile applications, misconfigured public cloud, Dark Web exposure or code repositories leaks.

The 2020 annual meeting of the World Economic Forum (WEF) urged the consideration of emerging cybersecurity challenges in the aviation industry, as addressed in its “Advancing Cyber Resilience in Aviation: An Industry Analysis” report.
To shed some light on the current state of aviation transportation security, we decided to conduct research on cybersecurity, compliance and privacy of some of the world's largest airports, many of which will be familiar to you.
Table of Content
2. Top 3 Most Secure Airports
3. Data Source
4. Testing Methodology
5. Website and Web Applications Security
6. Web Application Firewall Usage
7. Website TLS Encryption Security
8. PCI DSS and GDPR Website Compliance
9. Public Cloud Security
10. Mail Server Security
11. Mobile Applications and Backend APIs Security
12. Dark Web Exposure
13. Public Code Repositories Exposure
14. How to Reduce the Risks
Key findings
Main Website Security:
- 97% of the websites contain outdated web software
- 24% of the websites contain known and exploitable vulnerabilities
- 76% and 73% of the websites are not compliant with GDPR and PCI DSS respectively
- 24% of the websites have no SSL encryption or use obsolete SSLv3
- 55% of the websites are protected by a WAF
Mobile Application Security:
- 100% of the mobile apps contain at least 5 external software frameworks
- 100% of the mobile apps contain at least 2 vulnerabilities
- 15 security or privacy issues are detected per app on average
- 33.7% of the mobile apps outgoing traffic has no encryption
Dark Web Exposure, Code Repositories and Cloud:
- 66% of the airports are exposed on the Dark Web
- 72 out of 325 exposures are of a critical or high risk indicating a serious breach
- 87% of the airports have data leaks on public code repositories
- 503 out of 3184 leaks are of a critical or high risk potentially enabling a breach
- 3% of the airports have unprotected public cloud with sensitive data
Top 3 Most Secure Airports
During the research we identified 3 international airports that successfully passed all the tests without a single major issue being detected:
- Amsterdam Airport Schiphol (EU)
- Helsinki-Vantaa Airport (EU)
- Dublin Airport (EU)
They may serve a laudable example not just to the aviation industry but to all other industries as well.
Data Source
The research covers the world's Top 100 Airports (2019) from six global regions selected by Skytrax for the World Airport Awards:
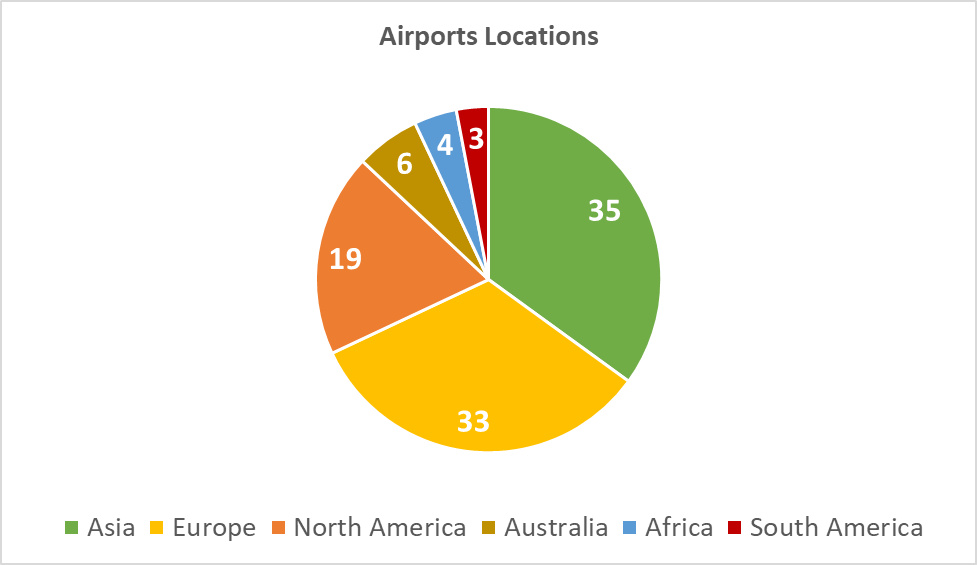
Diagram 1: Airports Locations
Testing Methodology
We leveraged an enhanced methodology from our previous research dedicated to application security of top banking institutions, including comprehensive coverage of their web, mobile and API security. The methodology of this research was also complemented with OSINT-based:
- Discovery and non-intrusive security testing of public cloud storages (e.g. AWS S3)
- Monitoring of Dark Web exposure (e.g. marketplaces and forums)
- Monitoring of public code repositories (e.g. GitHub)
The following external IT assets of the airports were detected and tested for security, compliance and privacy in a non-intrusive manner during the research:
| Tested Assets | Quantity |
|---|---|
| Main websites (the “www.” domain) | 100 |
| Subdomains (e.g. “subdomain.example.com”) | 1,346 |
| Official mobile applications | 36 |
| Backend APIs of the mobile applications | 244 |
| External Public Cloud Storage | 13 |
| External SaaS/PaaS Services | 95 |
Most of the leveraged testing tools are freely available online and can be used to reproduce the results of the research, as well as to monitor for improvements:
- SSL Security Test [scoring methodology and list of checks]
- Website Security Test [scoring methodology and list of checks]
- Mobile App Security Test [list of checks]
Our testing for PCI DSS compliance covered Requirements 2.3, 4.1, 6.2, 6.5 and 6.6 of the most recent version 3.2.1 of the standard (assuming the website falls within the Cardholder Data Environment).
Our testing for GDPR compliance covered Article 5 Section 1, Article 5 Section 2, Article 6 Section 1, Article 6 Section 4(e), Article 7, Article 25 Section 1, Article 32 Section 1(a)(b)(d) and Article 35 Section 7(f) of the enacted regulation (assuming website handles and/or store PII of the EU residents).
For the purpose of Dark Web Monitoring, Attack Surface Management (that included discovery of PaaS, SaaS and Private/Public Cloud Storages) and code repositories crawling we leveraged our ImmuniWeb Discovery technology.
Website and Web Applications Security
Application weaknesses and software vulnerabilities continue to be the most common means by which cybercriminals carry out external attacks says Forrester in its recent research.
Regrettably, only 3 main (“www.”) websites of the airports received the best possible “A+” grade, 15 got an “A” grade:
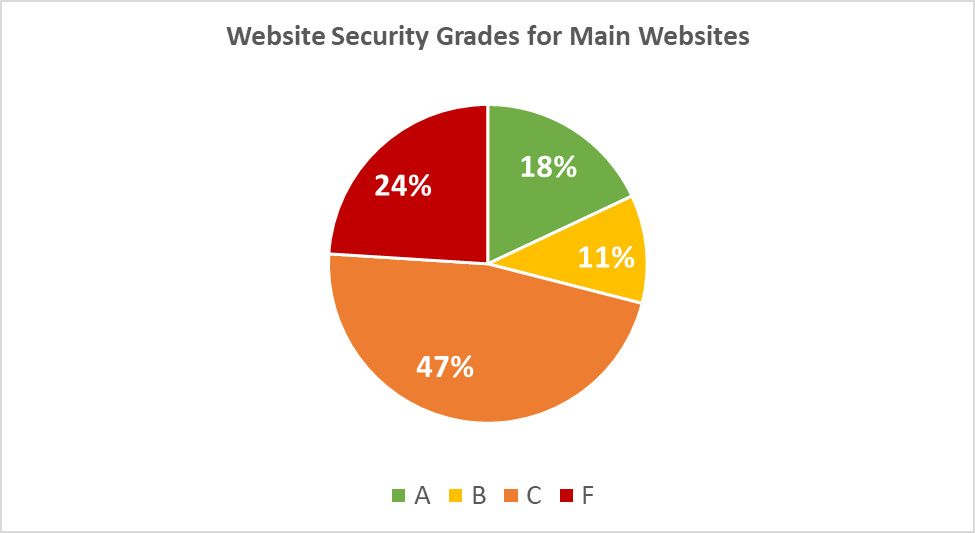
Diagram 2: Website Security Grades for Main Websites
Below is a detailed security scoring for the main websites of the airports:
| Grade | Quantity | Description |
|---|---|---|
| A+ | 3 | No single issue or misconfiguration |
| A | 15 | Minuscule issues found or slightly insufficient security hardening |
| B | 11 | Several minor issues or insufficient security hardening |
| C | 47 | Security vulnerabilities or several serious misconfigurations found |
| F | 24 | Exploitable and publicly known security vulnerabilities found |
As many as 24 of the main websites had a failing “F” grade, meaning that they had an outdated software with known and exploitable security vulnerabilities in CMS (e.g. WordPress) and/or web component (e.g. jQuery). Some of the websites even had several vulnerable components as detailed below:
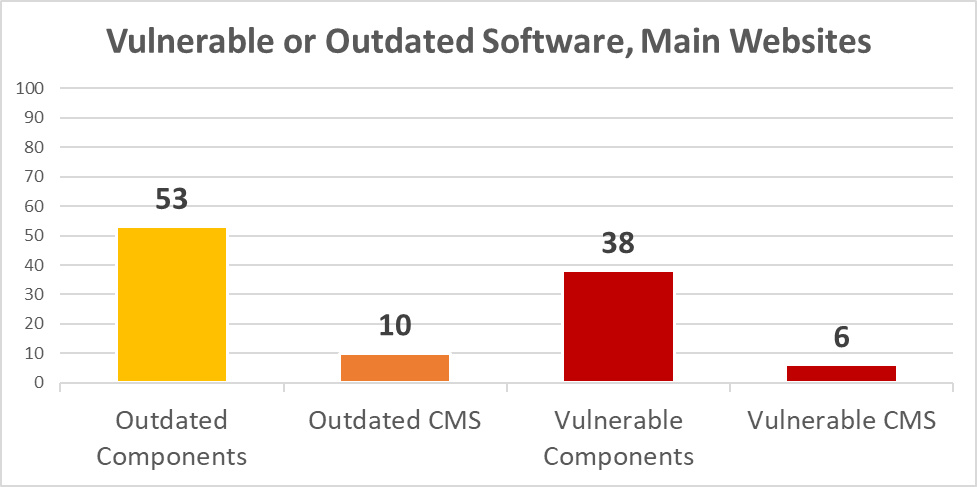
Diagram 3: Vulnerable or Outdated Software, Main Websites
As for the subdomains, we observed merely 17% of the web applications scored an “A” grade, while the majority had a border-to-failure “C” grade:
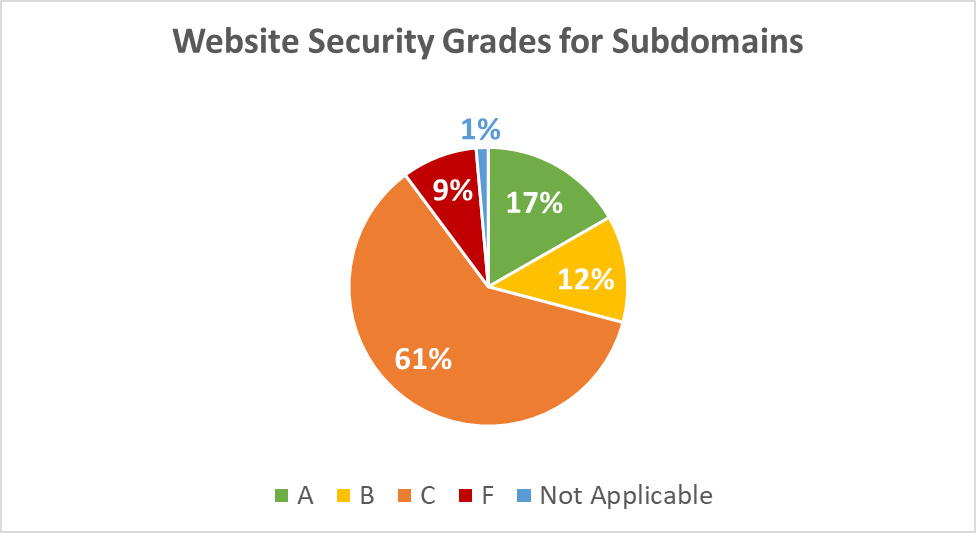
Diagram 4: Website Security Grades for Subdomains
Web Application Firewall Usage
Gartner says that the Web Application Firewall (WAF) market is growing, driven by adoption of cloud web application and API protection services.
However, WAFs are modestly present on the web applications run by the world's largest airports. Only 55% of the main websites and 40% of the subdomains are protected with a WAF:
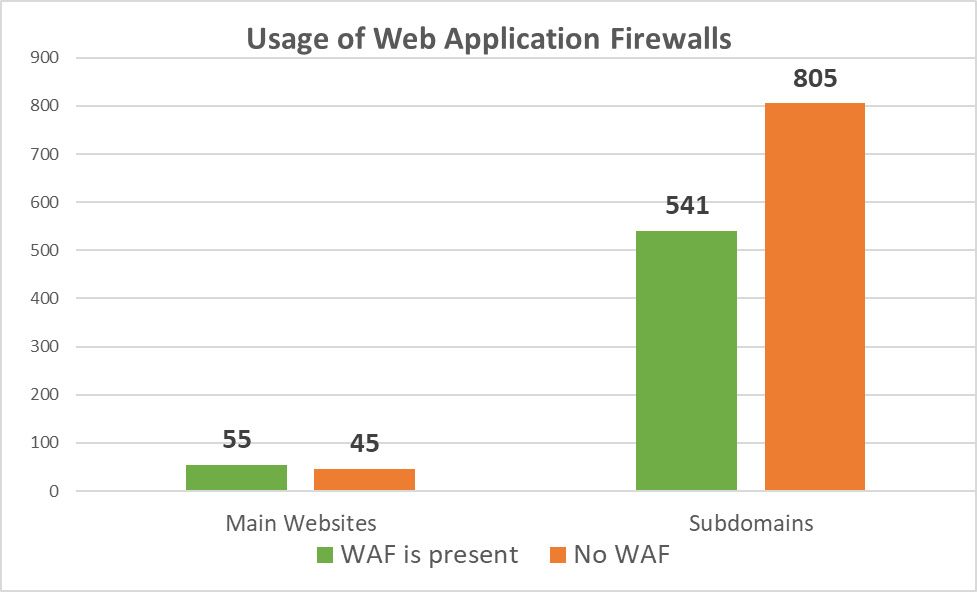
Diagram 5: Usage of Web Application Firewalls
Oftentimes, organizations regard a WAF through a prism of hindering their business by blocking requests from legitimate users, and simply disable this indispensable security control.
Website TLS Encryption Security
Holistic implementation of a reliable HTTPS TLS encryption ensures privacy and better security for the website visitors. However, as low as 15 out of 100 main websites of the airports marked the highest “A+” grade. 38 got “A” grades.
As many as 24 main websites do not use SSL/TLS encryption (“N” grade) or use obsolete SSLv3 protocol (or have another major problem), and scored with the failing “F” grade:
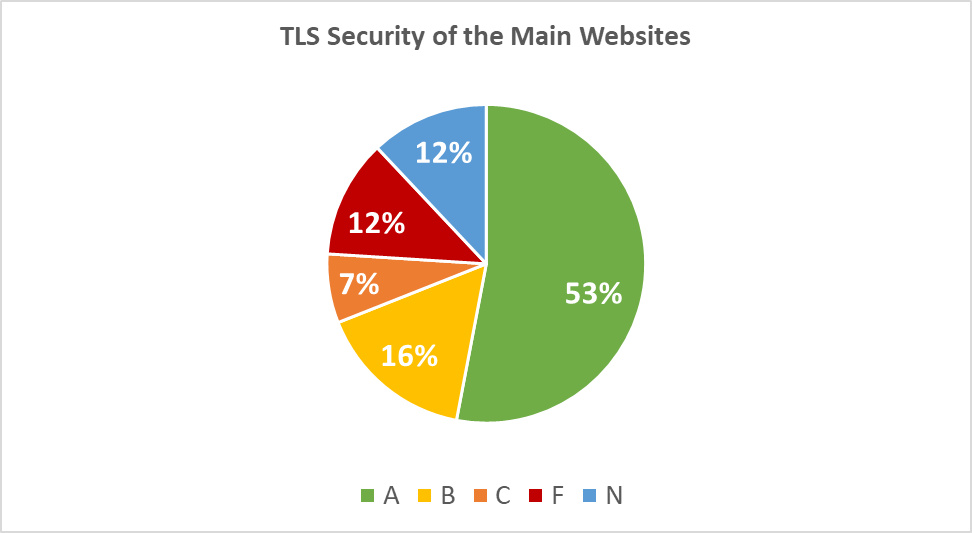
Diagram 6: TLS Security of the Main Websites
Below is a detailed security scoring for the main websites of the airports:
| Grade | Quantity | Description |
|---|---|---|
| A+ | 15 | No single issue or misconfiguration found |
| A | 38 | Minuscule issues found or slightly insufficient encryption hardening |
| B | 16 | Several minor issues or insufficient encryption hardening |
| C | 7 | Security vulnerabilities or several serious misconfigurations found |
| F | 12 | SSLv3 or an exploitable security vulnerability found |
| N | 12 | No encryption |
The situation is, however, substantially worse with the subdomains, where 308 websites failed with an “F”, and 75 do not use the encryption:
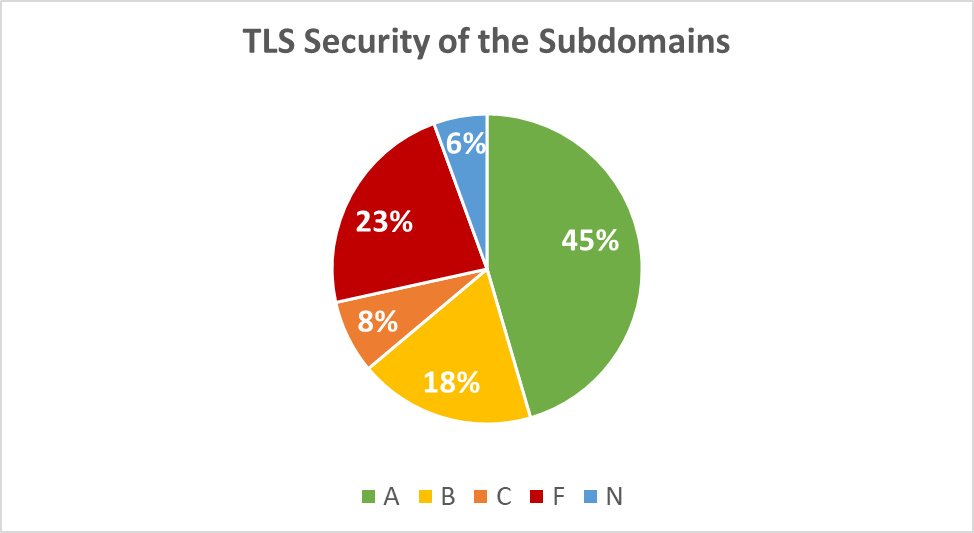
Diagram 7: TLS Security of the Subdomains
Below is a detailed security scoring for the subdomains of the airports:
| Grade | Quantity | Description |
|---|---|---|
| A+ | 188 | No single issue or misconfiguration found |
| A | 424 | Minuscule issues found or slightly insufficient encryption hardening |
| B | 248 | Several minor issues or insufficient encryption hardening |
| C | 103 | Security vulnerabilities or several serious misconfigurations found |
| F | 308 | SSLv3 or an exploitable security vulnerability found |
| N | 75 | No encryption |
PCI DSS and GDPR Website Compliance
Even if PCI DSS compliance is not always applicable or requisite, GDPR compliance seems to be vital for the international airports. Moreover, both PCI DSS and GDPR requirements cover the foundational security aspects (cf. methodology above) that should not be neglected by anyone, even if compliance is not required.
Since its implementation in May 2018, GDPR has led to over 160,000 data breach notifications across Europe, with 114 million euros ($126 million) in imposed fines, says CNBC. Alarmingly, only 27 main websites comply with the applicable PCI DSS requirements:
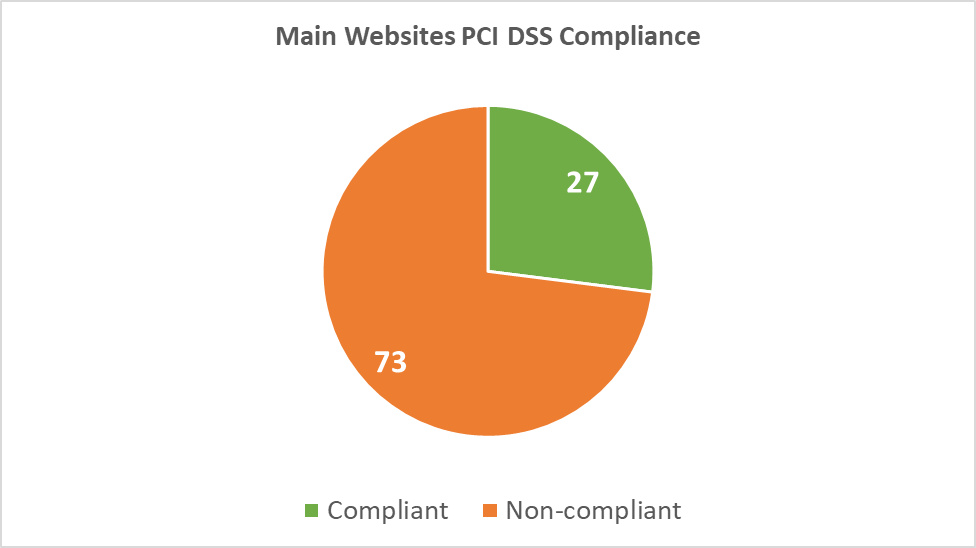
Diagram 8: Main Websites PCI DSS Compliance
As for the applicable GDPR requirements, only 24% (24/100) of the main websites and 12% (158/1346) of the subdomains comply:
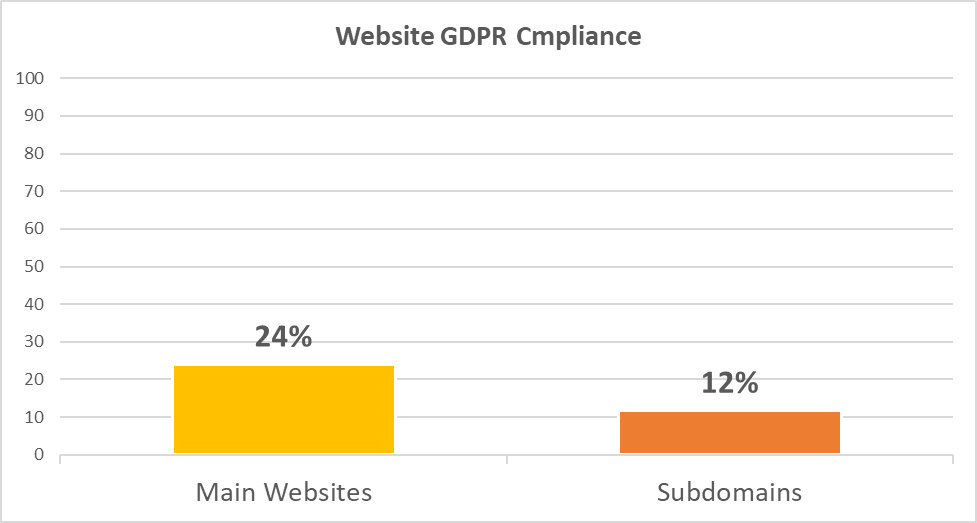
Diagram 9: Websites GDPR Compliance
Public Cloud Security
2019 was marked by a grim variety of countless security incidents and disastrous data breaches caused by unprotected or misconfigured public cloud storage, frequently involving Amazon’s AWS S3 infrastructure.
A quick scan for public clouds revealed usage of AWS S3 public cloud storage by 12 airports. 3 airports had buckets that were publicly accessible and contained a considerable volume of visibly sensitive data. All of this is despite a major security hardening by Amazon announced over a year ago, aimed at making S3 secure by default.
The global airports also actively rely on various third-party SaaS and PaaS solutions, such as Monday Project Management or Heroku. 33 airports rely on third parties to process or store potentially sensitive data, having in total 88 different solutions deployed. Security testing of these solutions may be intrusive and is therefore beyond the scope of this research.
Mail Server Security
During the research, we were able to identify 147 mail servers that are used to accept or relay emails. Nearly half of mail servers (48%) do not support SSL/TLS encryption, which makes it very easy for an attacker to perform a Man-in-the-Middle (MitM) attack, intercept traffic and read email communication in plain text.
Roughly 21% of the mail servers (32) scored an “A” grade. The remaining 44 servers had poor of vulnerable implementation of SSL/TLS, mostly with “C” and failing “F” grades:
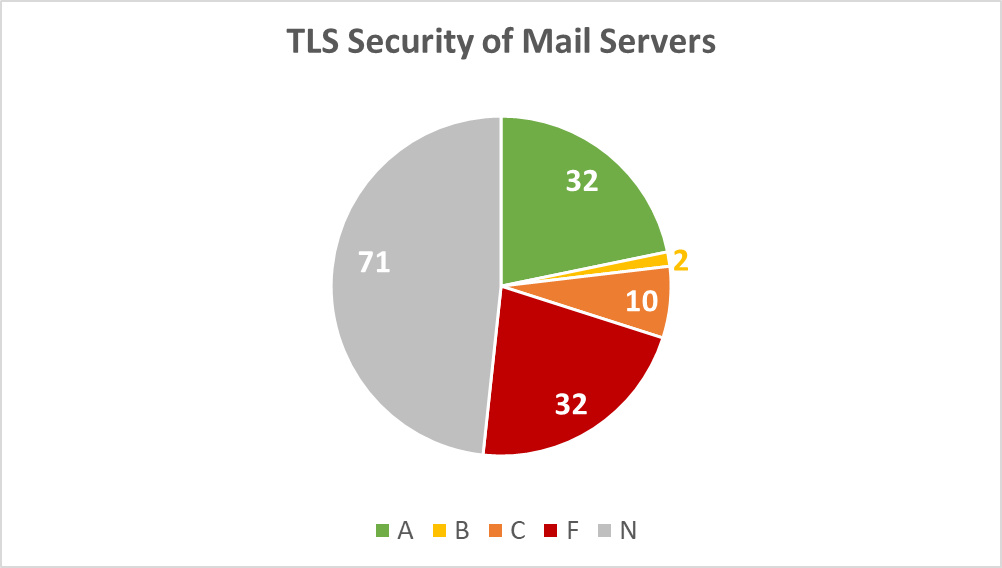
Diagram 10: TLS Security of Mail Servers
Organizations are well aware of the necessity to harden SSL/TLS encryption of their websites, but largely neglect their email servers. By using our free SSL test you can easily test your IMAPS, POP3S, SMTPS and STARTTLS email servers for security and privacy issues.
Mobile Applications and Backend APIs Security
Denise Lund, Research Director, Enterprise Mobility Research at IDC, says: "There are few businesses for whom a proven MAST (Mobile Application Security Testing) software solution cannot benefit its time, cost, and risk profile today and for the foreseeable future."
During this research, we found and tested 36 official mobile applications belonging to the airports. In total, 530 security and privacy issues were identified, including 288 mobile security flaws (15 per application on average). Below is a risk mapping (based on CVSSv3 scoring) for the detected vulnerabilities:
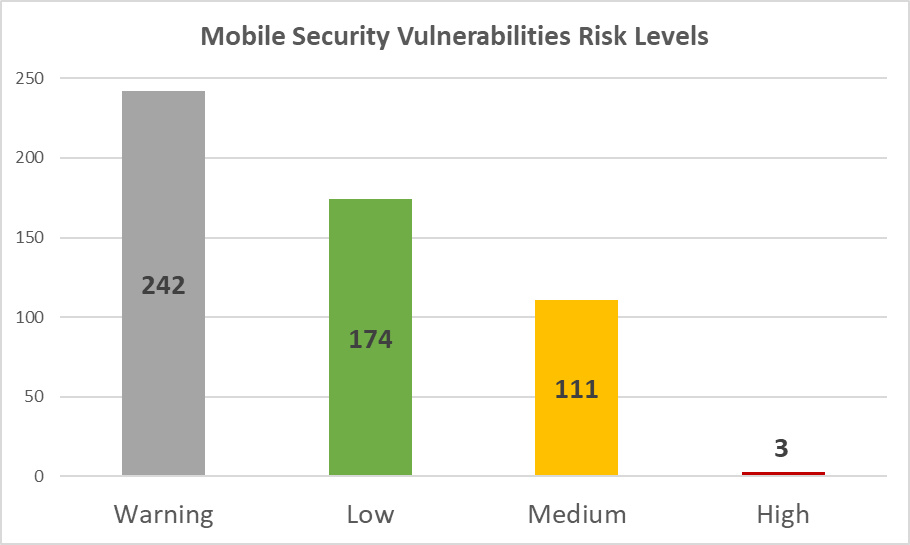
Diagram 11: Mobile Security Vulnerabilities Risk Levels
The next diagram demonstrates distribution of the discovered issues mapped according to the OWASP Top 10 Mobile risks and weaknesses. M1 (Improper Platform Usage) and M2 (Insecure Data Storage) were present in every single application and are the most popular security flaws affecting the applications:
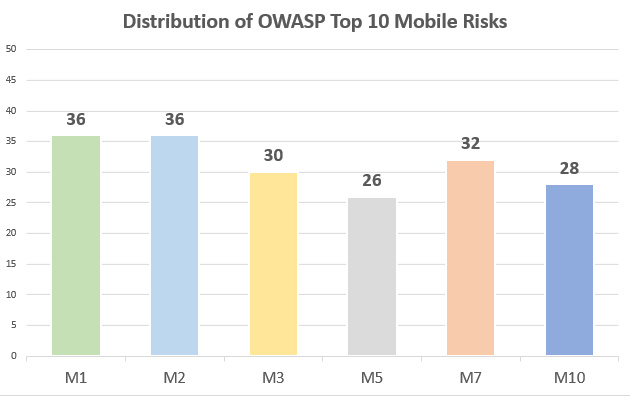
Diagram 12: Distribution of OWASP Top 10 Mobile Risks
As for the mobile backends (e.g. Web Services or APIs), only 55% of the outgoing connections use proper TLS encryption to protect user data in transit.
27% of the connections send the information in plaintext and do not use encryption at all (“N” grade), and 5.7% are into obsolete and vulnerable SSLv3 protocol ending up with the failing “F” grade:
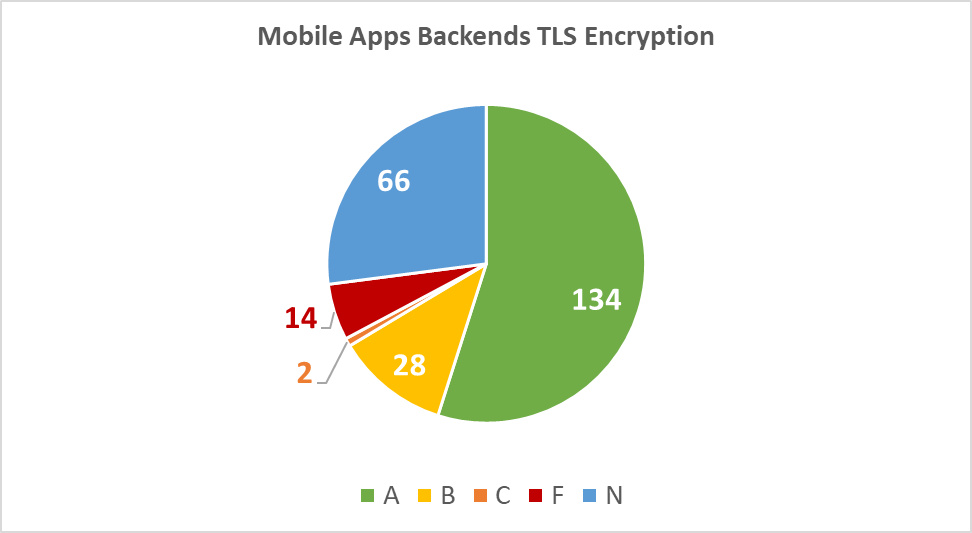
Diagram 13: Mobile Apps Backends TLS Encryption
Dark Web Exposure
Compared to the Fortune 500 companies' exposure, the global airports are doing fairly well. For the purpose of this research, we leveraged our award-winning AI technology to distill findings from the Dark Web marketplaces and other locations, notably to remove duplicates, fakes and irrelevant findings.
After purification of the results, we found that 66 out of the 100 airports are exposed on the Dark Web in one way or another. As shown on the diagram below, 13 airports have leaks or exposures of a critical risk:
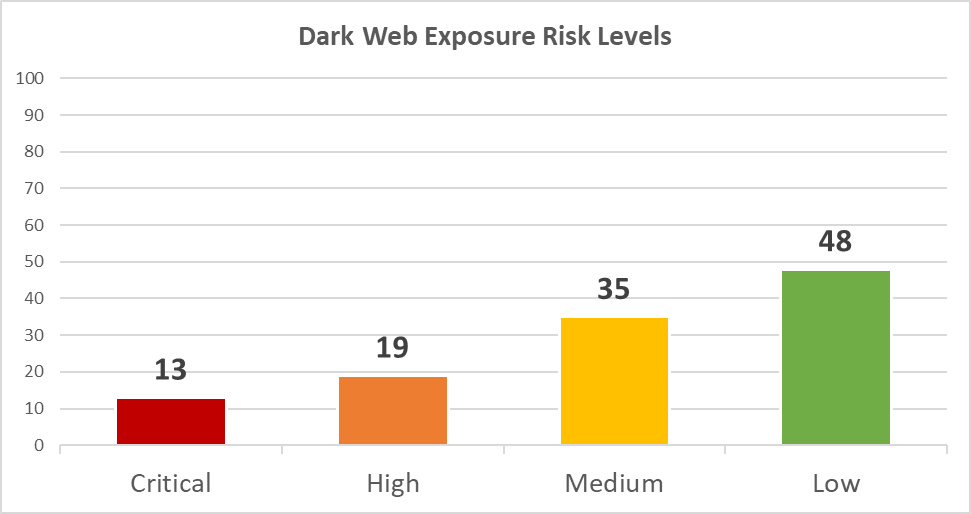
Diagram 14: Dark Web Exposure Risk Levels
Below is a brief summary and explanations of the risks related to the Dark Web exposure:
| Risk | Number of airports | Quantity of exposures | Description |
|---|---|---|---|
| Critical | 13 | 30 | Recent leak of highly confidential data (e.g. PII, PHI, IDs, financial records, plaintext passwords for production systems, etc.) |
| High | 19 | 42 | Recent leak of confidential data (e.g. PII, accounts from third party systems, etc.) |
| Medium | 35 | 79 | Leak of internal or sensitive data (e.g. source codes, documents, records, etc.) |
| Low | 48 | 174 | Leak of outdated or low-criticality data (e.g. non-public technical documentation) |
Public Code Repositories Exposure
A week ago, AWS reportedly leaked exposed passwords and private keys on GitHub to continue a lingering set of security incidents related to public code repositories.
Nowadays, increasingly more companies and organizations rely on public code repositories to share code, and the world's largest airports are no exception. In light of the omnipresent proliferation of CI/CD and DevOps across the globe, 87 out of 100 airports had some sensitive or internal data exposed at various public code repositories, such as GitHub or Bitbucket. Amongst them, 59 airports were identified with 227 code leakages of a critical risk:
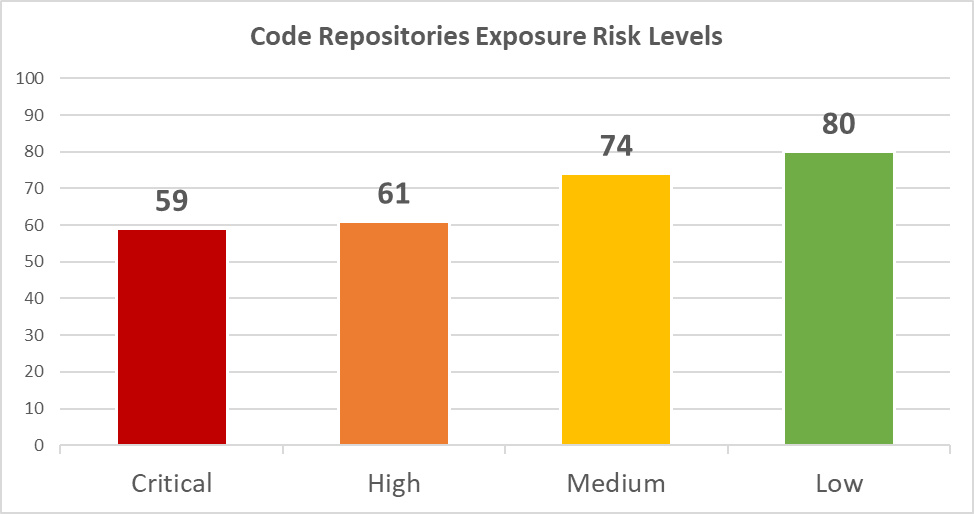
Diagram 15: Code Repositories Exposure Risk Levels
Below is a brief summary and explanations of the risks related to the Code Repositories exposure:
| Risk | Number of airports | Quantity of issues | Description |
|---|---|---|---|
| Critical | 59 | 227 | Confidential information disclosure (e.g. hardcoded passwords, API keys, private tokens, etc.) |
| High | 61 | 306 | Sensitive information disclosure (e.g. password from third-party systems, internal source code, etc.) |
| Medium | 74 | 995 | Internal information disclosure (e.g. config files, internal paths or schemas, etc.) |
| Low | 80 | 1656 | Debugging or technical information (e.g. ToDo lists, bug reports, internal discussions of developers, etc.) |
How to Reduce the Risks
- Implement a continuous security monitoring system with anomaly detection to spot intrusions, phishing and password re-use attacks.
- Run a continuous discovery and inventory of your digital assets, visualize your external attack surface and risk exposure with an Attack Surface Management (ASM) solution enhanced with Dark Web and code repositories monitoring.
- Implement a holistic, DevSecOps-enabled application security program to test and remediate your web and mobile applications, APIs and OSS in a timely manner
- Implement a third-party risk management program encompassing continuous monitoring of your vendors and suppliers going beyond a paper-based questionnaire.
- Invest into security awareness of your personnel, explain the risks of using professional emails on third-party resources, gamify anti-phishing training and reward the best learners.
Visualize your external attack surface and Dark Web exposure with ImmuniWeb® Discovery.
What’s next:
- Request your interactive demo
- Follow ImmuniWeb on Twitter and LinkedIn
- Learn more about Attack Surface Management by ImmuniWeb® Discovery
- Learn more about AI-enabled Application Security Testing by ImmuniWeb
- Learn more about ImmuniWeb Community Edition




