CWE Glossary
- CWE-22: Path Traversal
- CWE-78: OS Command Injection
- CWE-79: Cross-Site Scripting
- CWE-89: SQL Injection
- CWE-90: LDAP Injection
- CWE-91: XML Injection
- CWE-94: Code Injection
- CWE-98: PHP File Inclusion
- CWE-113: HTTP Response Splitting
- CWE-119: Buffer Errors
- CWE-130: Improper Handling of Length Parameter Inconsistency
- CWE-193: Off-by-one Error
- CWE-200: Information Exposure
- CWE-211: Information Exposure Through Externally-Generated Error Message
- CWE-236: Improper Handling of Undefined Parameters
- CWE-276: Incorrect Default Permissions
- CWE-284: Improper Access Control
- CWE-285: Improper Authorization
- CWE-287: Improper Authentication
- CWE-297: Improper Validation of Certificate with Host Mismatch
- CWE-306: Missing Authentication for Critical Function
- CWE-312: Cleartext Storage of Sensitive Information
- CWE-345: Insufficient Verification of Data Authenticity
- CWE-352: Cross-Site Request Forgery
- CWE-384: Session Fixation
- CWE-427: Uncontrolled Search Path Element
- CWE-434: Unrestricted Upload of File with Dangerous Type
- CWE-476: NULL Pointer Dereference
- CWE-521: Weak Password Requirements
- CWE-601: Open Redirect
- CWE-611: Improper Restriction of XML External Entity Reference ('XXE')
- CWE-613: Insufficient Session Expiration
- CWE-618: Exposed Unsafe ActiveX Method
- CWE-671: Lack of Administrator Control over Security
- CWE-798: Use of Hard-coded Credentials
- CWE-799: Improper Control of Interaction Frequency
- CWE-822: Untrusted Pointer Dereference
- CWE-835: Infinite Loop
- CWE-918: Server-Side Request Forgery (SSRF)
- CWE-942: Overly Permissive Cross-domain Whitelist
CWE is a trademark of the MITRE Corporation.
Improper Handling of Undefined Parameters [CWE-236]
Improper Handling of Undefined Parameters describes a case when application uses undefined parameter, field, or argument.
![Improper Handling of Undefined Parameters [CWE-236] Improper Handling of Undefined Parameters [CWE-236]](/images/vulnerability/previews/improper-handling-of-undefined-parameters-cwe-236.jpg)
Created: December 4, 2012
Latest Update: December 15, 2020
Table of Content
- Description
- Potential impact
- Attack patterns
- Affected software
- Severity and CVSS Scoring
- Mitigations
- References
Want to have an in-depth understanding of all modern aspects of Improper Handling of Undefined Parameters [CWE-236]? Read carefully this article and bookmark it to get back later, we regularly update this page.
1. Description
This weakness occurs when software performs actions on parameters, fields, or arguments that are not defined or are unexpected. This error is usually spotted when certain actions are performed on arrays with arbitrary number of elements or keys. The impact of this weakness can vary depending on application design and exploitation conditions. The attacker might be able to crash the application, modify data or even execute arbitrary code.
We will use a simple example to demonstrate this vulnerability. The code below expects a serial number from a command line and compares it against the hardcoded value.
- // Improper Handling of Undefined Parameters [CWE-236] vulnerable code example
- // (c) HTB Research
- #include "StdAfx.h"
- #ifdef WIN32
- #include <windows.h>
- #else
- #include <string.h>
- #endif
- #include <stdio.h>
- #define SERIAL "ABCD907341AB"
- void CompareStrings(char * DATA, char * DATA2)
- {
- if(strcmp(DATA, DATA2) == 0)
- {
- printf("The serial code is valid!\n");
- return;
- } else {
- printf("The serial code is invalid!\n");
- }
- return;
- }
- int CheckRegistration(char *InputKey)
- {
- CompareStrings (SERIAL, InputKey);
- return 0;
- }
- int main(int argc, char* argv[])
- {
- // Call our function.
- CheckRegistration (argv[1]);
- return 0;
- }
The comparison results are shown on the following images:
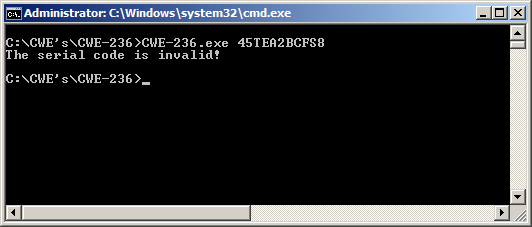
Figure - The user's entry code is invalid
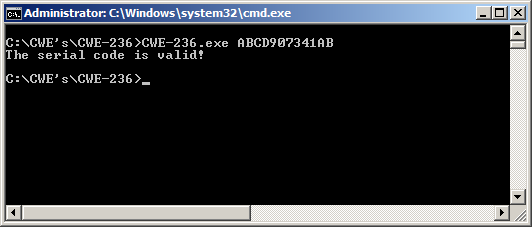
Figure - The user's entry code is valid
Our example, however, does not perform checks on the number of input parameters before calling the CheckRegistration() function. If the application is executed without arguments, a value of NULL is passed as an "InputKey" argument of the CompareStrings() function, which is later used in the strcmp() call. As a result, the application crashes with exception code c0000005.
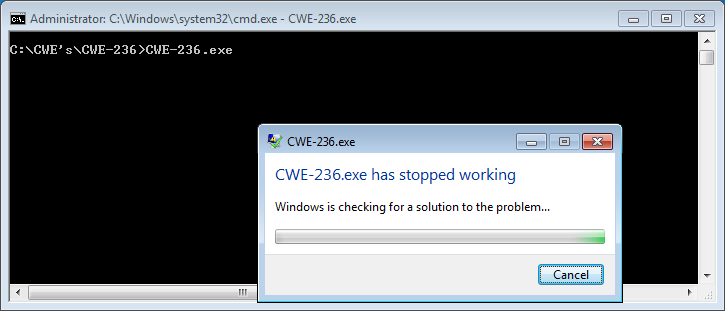
Figure - The application crashes due to an undefined parameter
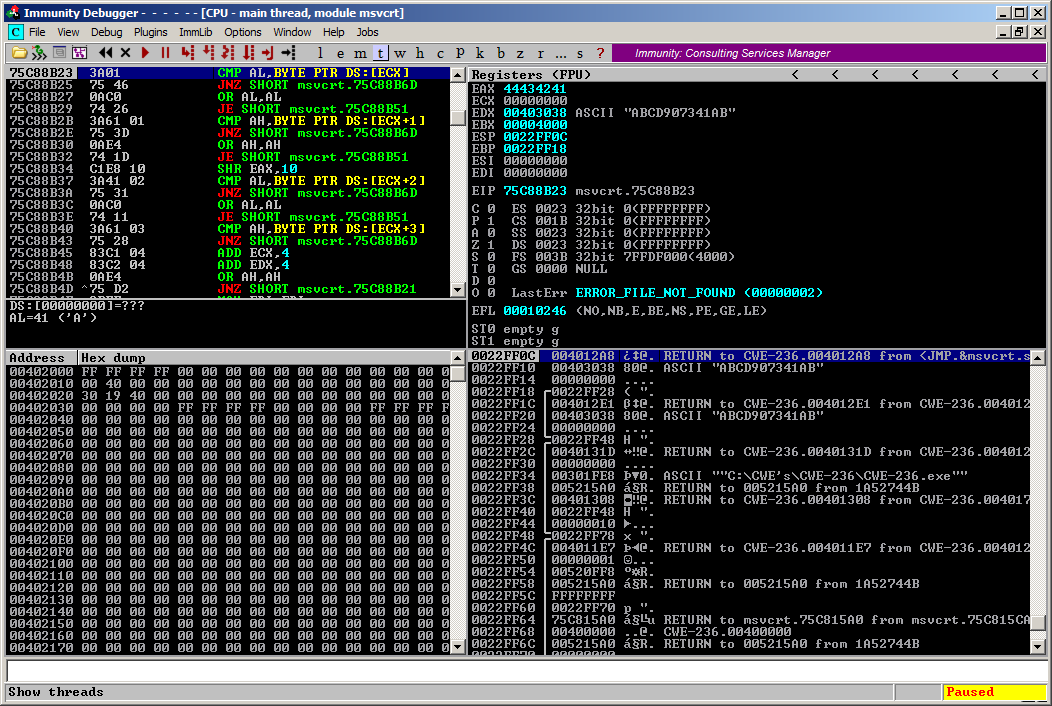
Figure - The application crashes due to an undefined parameter
2. Potential impact
The attacker who controls input parameters can influence the application flaw. This can trigger an unexpected behavior of the application and lead to a crash, information leak, data tampering or code execution.
3. Attack patterns
There are no particular CAPEC attack patterns assigned to this weakness.
4. Affected software
This weakness can be introduced into the application during architecture, design, or implementation phase and is language independent. This means that any language can be susceptible to this issue.
5. Severity and CVSS Scoring
This weakness can have different impacts and should be scored in accordance to them.
Information disclosure
If there is a possibility to disclose certain parts of memory, the weakness should be scored as C:L/I:N/A:N.
In case of a remote attack against client application, the CVSS score is as follows:
5.3 [CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:N/A:N] – Medium Severity.
Denial of service
If vulnerability is present in a software and exploitation of buffer overflow results in application crash it should be scored as C:N/I:N/A:H. But if the vulnerability could be used to crash or reboot the entire system it should be scored as S:C as well.
The following example can be used to score remotely exploitable vulnerability in a network service, which runs with SYSTEM privileges:
8.6 [CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:C/C:N/I:N/A:H] – High Severity.
Code execution
If there is a possibility of code execution, the CVSS score should be C:H/I:H/A:H. For a remote attack vector, we recommend usage of the following CVSS metrics:
9.8 [CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H] – Critical Severity.
6. Mitigations
This type of weakness does not have particular mitigation techniques. Developers should carefully manage untrusted input and pay attention to arguments that are passed to the application.
7. References
- CWE-236: Improper Handling of Undefined Parameters [cwe.mitre.org]
- Nero MediaHome Server Multiple Remote DoS Vulnerabilities [HTB23130] [htbridge.com]
Copyright Disclaimer: Any above-mentioned content can be copied and used for non-commercial purposes only if proper credit to ImmuniWeb is given.
↑ Back to Top
