CWE Glossary
- CWE-22: Path Traversal
- CWE-78: OS Command Injection
- CWE-79: Cross-Site Scripting
- CWE-89: SQL Injection
- CWE-90: LDAP Injection
- CWE-91: XML Injection
- CWE-94: Code Injection
- CWE-98: PHP File Inclusion
- CWE-113: HTTP Response Splitting
- CWE-119: Buffer Errors
- CWE-130: Improper Handling of Length Parameter Inconsistency
- CWE-193: Off-by-one Error
- CWE-200: Information Exposure
- CWE-211: Information Exposure Through Externally-Generated Error Message
- CWE-236: Improper Handling of Undefined Parameters
- CWE-276: Incorrect Default Permissions
- CWE-284: Improper Access Control
- CWE-285: Improper Authorization
- CWE-287: Improper Authentication
- CWE-297: Improper Validation of Certificate with Host Mismatch
- CWE-306: Missing Authentication for Critical Function
- CWE-312: Cleartext Storage of Sensitive Information
- CWE-345: Insufficient Verification of Data Authenticity
- CWE-352: Cross-Site Request Forgery
- CWE-384: Session Fixation
- CWE-427: Uncontrolled Search Path Element
- CWE-434: Unrestricted Upload of File with Dangerous Type
- CWE-476: NULL Pointer Dereference
- CWE-521: Weak Password Requirements
- CWE-601: Open Redirect
- CWE-611: Improper Restriction of XML External Entity Reference ('XXE')
- CWE-613: Insufficient Session Expiration
- CWE-618: Exposed Unsafe ActiveX Method
- CWE-671: Lack of Administrator Control over Security
- CWE-798: Use of Hard-coded Credentials
- CWE-799: Improper Control of Interaction Frequency
- CWE-822: Untrusted Pointer Dereference
- CWE-835: Infinite Loop
- CWE-918: Server-Side Request Forgery (SSRF)
- CWE-942: Overly Permissive Cross-domain Whitelist
CWE is a trademark of the MITRE Corporation.
Insufficient Verification of Data Authenticity [CWE-345]
Insufficient Verification of Data Authenticity weakness describes improper or absent verification of input data authenticity.
![Insufficient Verification of Data Authenticity [CWE-345] Insufficient Verification of Data Authenticity [CWE-345]](/images/vulnerability/previews/insufficient-verification-of-data-authenticity-cwe-345.jpg)
Created: December 11, 2013
Latest Update: December 28, 2020
Table of Content
- Description
- Potential impact
- Attack patterns
- Affected software
- Exploitation Examples
- Severity and CVSS Scoring
- Mitigations
- References
- Latest Related Security Advisories
Want to have an in-depth understanding of all modern aspects of Insufficient Verification of Data Authenticity [CWE-345]? Read carefully this article and bookmark it to get back later, we regularly update this page.
1. Description
This class of weaknesses is a result of trust issues between data exchange parties. If application fails to verify data origin or its authenticity, an attacker might be able to perform spoofing attacks against vulnerable application or its clients. Lack of data authenticity verification may arise in a variety of situations and most likely to be introduced at design and implementation stages of application development process.
CWE-345 should be considered as a class of weaknesses and it’s a parent element for such entries as Cross-sire Request Forgery.
In this paper we will try to cover most common cases of this weakness and provide possible workarounds and mitigation techniques.
Server-side vulnerabilities
Server applications are designed to work with multiple clients. If such application fails to correctly verify its clients, a malicious user might leverage this weakness and perform certain unauthorized actions.
1.1 User identity spoofing
As an example of this weakness we will use a simple PHP script that displays contents of a customer’s basket based on user and basket identifiers:
- <?php
- $BasketID = intval($_GET["id"]); // Basket identifier
- if ($BasketID):
- // Selecting records from MySQL database
- $rs = $DB->Query("select * from tbl_basket where id='".$BasketID."'");
- while ($ar = $rs->Fetch()):
- CBasket::DisplayItem($ar); // Displaying output using CBasket::DisplayItem() function
- endwhile;
- endif;
- ?>
An attacker who knows basket identifier can successfully view contents of arbitrary basket.
1.2 CWE:352 - Cross-site Request Forgery
The following example contains a simple HTML form that is used to leave comments for website owners:
- <form name="tstForm" action="/index.php" method="POST">
- <input type="text" name="sName" value="" />
- <textarea name="sText"></textarea>
- <input type="submit" name="btSubmit" value="Send!">
- </form>
The above form sends HTTP request to the /index.php script. The index.php script contains the following code:
- <?
- $sName = $_POST["sName"];
- $sText = $_POST["sText"];
- If ($sName && $sText && CUser::IsAuthorized())
- CComment::AddComment($sName, $sText);
- Else
- Echo "Error";
- ?>
The above code allows publication of a comment when certain conditions are met. If $sName and $sText variables are not empty and user is authenticated in application, the function CComment::AddComment will be executed and comment will be published. An attacker can trick victim into visiting a webpage that sends the same request to the application. If the victim is authenticated within this application, the comment will be published too.
Client-side vulnerabilities
Client applications that do not verify authenticity of server application are also prone to this weakness. Great example of this vulnerability in client-side applications is Man-in-the-Middle attack, where an attacker is able to spoof server identity and perform certain actions against clients.
2. Potential impact
An attacker who controls user input or is able to influence network connectivity can perform a variety of actions and gain access to potentially sensitive information or event execute arbitrary code on vulnerable system.
3. Attack patterns
An attacker might use the following attack patterns to exploit this weakness:
- CAPEC-4: Using Alternative IP Address Encodings
- CAPEC-111: JSON Hijacking (aka JavaScript Hijacking)
- CAPEC-141: Cache Poisoning
- CAPEC-142: DNS Cache Poisoning
- CAPEC-209: Cross-Site Scripting Using MIME Type Mismatch
- CAPEC-218: Spoofing of UDDI/ebXML Messages
- CAPEC-384: Application API Message Manipulation via Man-in-the-Middle
- CAPEC-385: Transaction or Event Tampering via Application API Manipulation
- CAPEC-386: Application API Navigation Remapping
- CAPEC-387: Navigation Remapping To Propagate Malicoius Content
- CAPEC-388: Application API Button Hijacking
- CAPEC-389: Content Spoofing Via Application API Manipulation
This weakness is partially described under WASC-37 (Session Fixation) in WASC Threat Classification.
4. Affected software
Any application that handles input data can be vulnerable to this weakness.
5. Exploitation Examples
We will demonstrate exploitation of insufficient validation of data authenticity against a popular content management system Bitrix Site Manager. Security advisory HTB23183 describes vulnerability in e-Store Module of Bitrix Site Manager.
/bitrix/modules/sale/general/basket.php script is using the BITRIX_SM_SALE_UID cookie to identify a guest user as shown on the image below:
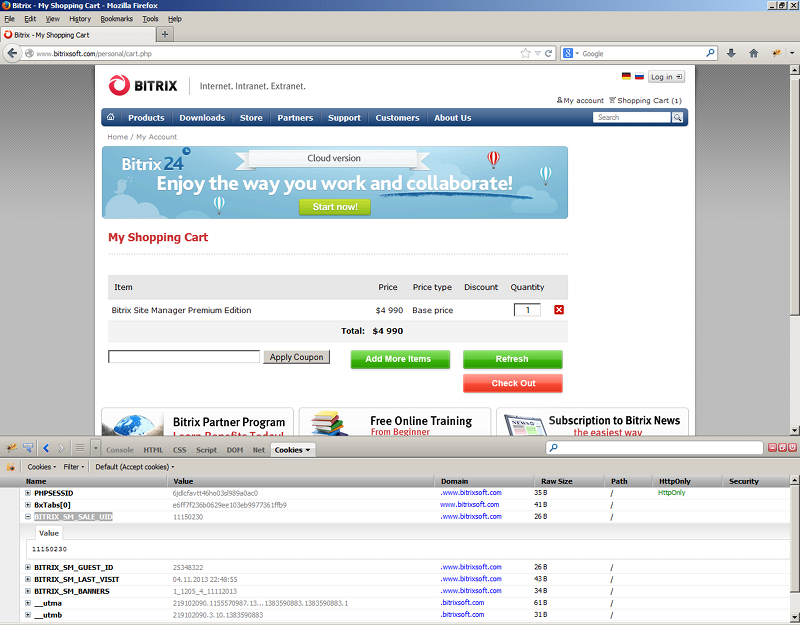
Let’s create a new order using different browser and then increase the value of the BITRIX_SM_SALE_UID cookie by 1:
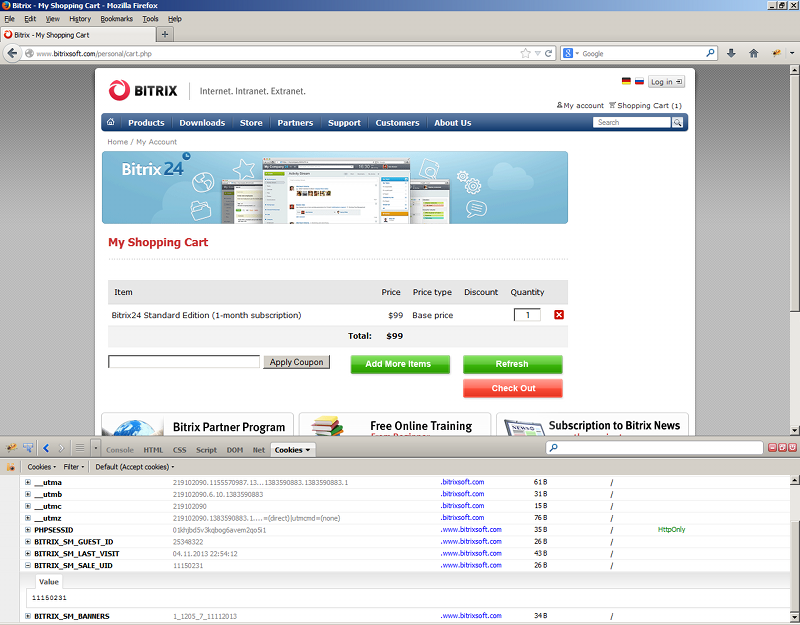
This example demonstrates how an attacker can spoof identity of a valid customer and view contents of arbitrary basket.
6. Severity and CVSS Scoring
Insufficient verification of data authenticity may lead to different impacts and should be scored considering maximum possible impact. Access complexity in client applications is usually set to medium due to possible complication in exploitation process.
Remote Code Execution
A remote code execution vulnerability in server application should be scored as follows:
9.3 (AV:N/AC:M/Au:N/C:C/I:C/A:C) – Critical severity.
Content Spoofing
4.3 (AV:N/AC:M/Au:N/C:N/I:P/A:N) – Medium severity.
Information Disclosure Vulnerability
4.3 (AV:N/AC:M/Au:N/C:P/I:N/A:N) – Medium severity.
Data Manipulation Vulnerability
6.8 (AV:N/AC:M/Au:N/C:P/I:P/A:P) – Medium severity.
7. Mitigations
The only way to protect application against this weakness is to perform additional checks on data authenticity. When developing the application consider all possible input data sources and use unique tokens to validate user input, always verify client and server identity.
8. References
- CWE-345: Insufficient Verification of Data Authenticity [cwe.mitre.org]
9. Insufficient Verification of Data Authenticity Vulnerabilities, Exploits and Examples
Copyright Disclaimer: Any above-mentioned content can be copied and used for non-commercial purposes only if proper credit to ImmuniWeb is given.
↑ Back to Top
