CWE Glossary
- CWE-22: Path Traversal
- CWE-78: OS Command Injection
- CWE-79: Cross-Site Scripting
- CWE-89: SQL Injection
- CWE-90: LDAP Injection
- CWE-91: XML Injection
- CWE-94: Code Injection
- CWE-98: PHP File Inclusion
- CWE-113: HTTP Response Splitting
- CWE-119: Buffer Errors
- CWE-130: Improper Handling of Length Parameter Inconsistency
- CWE-193: Off-by-one Error
- CWE-200: Information Exposure
- CWE-211: Information Exposure Through Externally-Generated Error Message
- CWE-236: Improper Handling of Undefined Parameters
- CWE-276: Incorrect Default Permissions
- CWE-284: Improper Access Control
- CWE-285: Improper Authorization
- CWE-287: Improper Authentication
- CWE-297: Improper Validation of Certificate with Host Mismatch
- CWE-306: Missing Authentication for Critical Function
- CWE-312: Cleartext Storage of Sensitive Information
- CWE-345: Insufficient Verification of Data Authenticity
- CWE-352: Cross-Site Request Forgery
- CWE-384: Session Fixation
- CWE-427: Uncontrolled Search Path Element
- CWE-434: Unrestricted Upload of File with Dangerous Type
- CWE-476: NULL Pointer Dereference
- CWE-521: Weak Password Requirements
- CWE-601: Open Redirect
- CWE-611: Improper Restriction of XML External Entity Reference ('XXE')
- CWE-613: Insufficient Session Expiration
- CWE-618: Exposed Unsafe ActiveX Method
- CWE-671: Lack of Administrator Control over Security
- CWE-798: Use of Hard-coded Credentials
- CWE-799: Improper Control of Interaction Frequency
- CWE-822: Untrusted Pointer Dereference
- CWE-835: Infinite Loop
- CWE-918: Server-Side Request Forgery (SSRF)
- CWE-942: Overly Permissive Cross-domain Whitelist
CWE is a trademark of the MITRE Corporation.
Incorrect Default Permissions [CWE-276]
Incorrect Default Permissions weakness describes a case where software sets insecure permissions to objects on a system.
![Incorrect Default Permissions [CWE-276] Incorrect Default Permissions [CWE-276]](/images/vulnerability/previews/incorrect-default-permissions-cwe-276.jpg)
Created: October 31, 2012
Latest Update: December 28, 2020
Table of Content
- Description
- Potential impact
- Attack patterns
- Affected software
- Exploitation Examples
- Severity and CVSS Scoring
- Mitigations
- References
- Latest Related Security Advisories
Want to have an in-depth understanding of all modern aspects of Incorrect Default Permissions [CWE-276]? Read carefully this article and bookmark it to get back later, we regularly update this page.
1. Description
This weakness describes a case where software sets unintended permissions to directories, files or other objects during installation process. As a result, a malicious user might be able to bypass intended security restrictions.
Most modern operating systems support access control lists (ACL) that are used to distinguish access rights for different users and groups. In modern operating systems a principal (e.g. process or threat acting on behalf of a user) acts upon objects. Access to these objects (e.g. files, directories, registry keys, etc.) is crucial for security mechanisms implemented in different operating systems and can influence system behavior depending on permissions imposed upon key components of the operating system.
1.1 Linux- / UNIX-based systems
General permissions
Access permissions in Linux and UNIX-like systems are based on three user classes (user, group, and others) and three access modes (read, write, and execute).
Ownership rights for each directory and file are set by the chown(1) and chgrp(1) commands and are based on user and group identifiers.
The following table demonstrates differences between access modes for directories and files:
| Read | Write | Execute | |
|---|---|---|---|
| Directory | Allows to view directory contents (e.g. with "ls" command) | Allows to delete and add new files | Allows to access files in the directory |
| File | Allows to view the file | Allows to write to the file | Allow to execute the file |
Setuid/setgid bit
Setuid and setgid bits are access flags used to run applications with permissions of the executable's owner or group respectively. Setuid/setgid bits are usually set for applications that need elevated privileges on the system, e.g. the ping command must send and listen for control packets on a network interface and thus needs elevated privileges, since regular user is not allowed to do so.
In our case the /bin/ping executable is owned by root. This means that having write-access to this executable might allow execution of arbitrary code on the system with root privileges. That's why it is very important to keep track of these files.
1.2 Windows-based systems
Support of access control lists starts with the NT family of Microsoft products and its NTFS file system. Before that only file attributes were used to distinguish access rights. All modern versions of Windows implement access control lists for directories, files, and registry keys. Proper system security depends on correct access rights.
Windows-based operating systems are equipped with graphical user interface (GUI) and command line utility to manage access rights. The GUI is accessible via Windows Explorer:
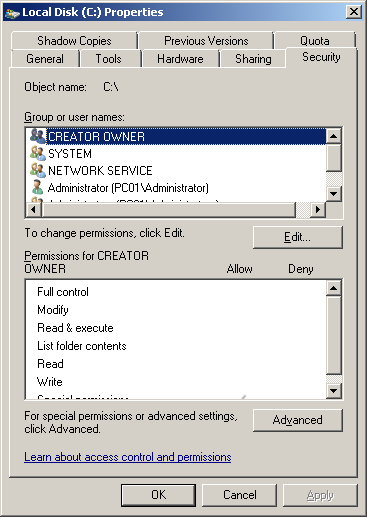
The "icacls" command line utility and its previous versions, such as "cacls" or "xcacls", can also be used to view and modify access rights for users and groups. The following command displays permissions for the "C:\" drive:
C:\Users\Administrator>icacls C:
C: PC01\Administrator:(F)
NT AUTHORITY\SYSTEM:(F)
BUILTIN\Administrators:(F)
PC01\Administrator:(OI)(CI)(IO)(F)
NT AUTHORITY\SYSTEM:(OI)(CI)(IO)(F)
BUILTIN\Administrators:(OI)(CI)(IO)(F)
Successfully processed 1 files; Failed processing 0 files
Access rights to registry keys are managed by the regedit.exe utility. Since Windows-based operating systems depend on system registry, having insecure permissions on keys and hives might weaken system security and allow an attacker to gain unauthorized control over the system.
2. Potential impact
Usually this weakness is locally exploitable. A malicious user might be able to gain access to sensitive information, tamper with sensitive data or compromise the vulnerable system entirely. If a setuid/setgid executable has world writable permissions any local user can inject malicious content into it and execute arbitrary code with privileges of the file's owner.
Basically, any application writable by an unintended actor poses a threat to system security and might be used to elevate privileges on the system, e.g. if such application was modified by a malicious and unprivileged user before being executed by a privileged one.
3. Attack patterns
The following CAPEC patterns correspond to this weakness:
- CAPEC-1: Accessing Functionality Not Properly Constrained by ACLs
- CAPEC-19: Embedding Scripts within Scripts
- CAPEC-81: Web Logs Tampering
- CAPEC-127: Directory Indexing
- CAPEC-169: Footprinting
Incorrect permissions vulnerability is described in WASC Threat Classification as a weakness under WASC-17 (Improper Filesystem Permissions).
4. Affected software
Software that changes access rights to objects during installation is potentially vulnerable to this weakness.
5. Exploitation Examples
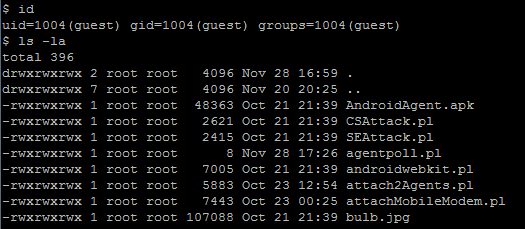
We will use the HTB23123 security advisory (CVE-2012-5697) as an example of this weakness. The vulnerability is introduced by the "btinstall" installation script that sets world-writable permissions for all files within the "/frameworkgui/" directory.
Let's login into the system under unprivileged guest account. To view files permissions we will execute the "ls –la" command, as demonstrated on the image below:
Now we will try to read the "config" file and then modify the agentpoll.pl script:
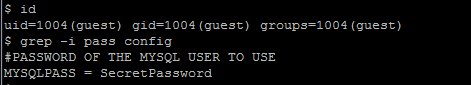
As a result of this vulnerability any local user has full access to files within the "/frameworkgui/" directory.
6. Severity and CVSS Scoring
Insecure default permissions are usually applied to locally installed applications, that's why the primary access vector is local system.
Information disclosure
In case of potential information disclosure (e.g. software configuration, credentials, etc.) this weakness should be scored as:
3.3 [CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:L/I:N/A:N] - Low severity.
Data tampering
This weakness could be used to tamper with potentially sensitive information such as log files. If data can be modified or deleted, it should be scored as:
5.3 [CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:L/I:L/A:L] - Medium severity.
System access
If an attacker can modify a setuid binary or any other file that can be executed by another user or service on the system, privilege escalation is possible. In this case this weakness should be scored as:
8.8 [CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H] - High severity.
7. Mitigations
Handling access rights is tricky, especially when software vendors are not doing it properly.
Linux- / UNIX-based systems
Manage carefully user and group ownership for files and folders. Never let unintended groups access restricted information. Use /bin/ls command to view effective permissions for directories and files. Use chown and chgrp commands to set appropriate ownership rights.
Avoid 777 permissions on files and folders, unless absolutely necessary, that all local users have read, write, and execute permissions to these files. Use chmod command to set appropriate permissions.
Keep track of setuid / setgit executables.
The following command lists all setuid and setgid files on the system:
# find / -type f -perm /6000To list all setuid and setgid files that are world writable execute the following command:
# find . -type f -perm /6000 -a -perm -0002If the above command lists files, this means a great threat for system security. It is recommended to change permissions for the listed files and perform full system audit. The system might be already compromised.
Windows-based systems
Keep track of permissions installed by software for directories, files, and registry keys during installation.
Never let applications set world writable permissions to executable files, especially within the system PATH environment variable or any other default search path, e.g. Windows, Windows/system32 directories, etc.
Keep track of permissions for registry keys that are used to automatically launch applications during system startup, e.g. HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run, HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce, etc.
8. References
- CWE-276: Incorrect Default Permissions [cwe.mitre.org]
- Understanding Windows File And Registry Permissions [msdn.microsoft.com]
- File Access Permissions [linuxfocus.org]
- Configuring Unix / Linux File and Directory Access Rights [netsecurity.about.com]
- Filesystem permissions [wikipedia.org]
- Linux Files and File Permission [comptechdoc.org]
9. Incorrect Default Permissions Vulnerabilities, Exploits and Examples
- HTB23198: Multiple Vulnerabilities in Eventum
- HTB23123: Multiple Vulnerabilities in Smartphone Pentest Framework (SPF)
Copyright Disclaimer: Any above-mentioned content can be copied and used for non-commercial purposes only if proper credit to ImmuniWeb is given.
↑ Back to Top
